List of military tactics
The meaning of the phrase is context sensitive, and has varied over time, like the difference between "strategy" and "tactics".[1]
| Part of a series on |
| War |
|---|
|
|
|
Related
|
This page contains a list of military tactics.
General
- Exploiting prevailing weather – the tactical use of weather as a force multiplier has influenced many important battles throughout history, such as the Battle of Waterloo.[2]
- Fire attacks – reconnaissance by fire is used by apprehensive soldiers when they suspect the enemy is nearby.
- Force concentration – the practice of concentrating a military force against a portion of an enemy force.[3]
- Night combat – combat that takes place at night. It often requires more preparation than combat during daylight and can provide significant tactical advantages and disadvantages to both the attacker and defender.[4]
- Reconnaissance – a mission to obtain information by visual observation or other detection methods, about the activities and resources of the enemy or potential enemy, or about the meteorologic, hydrographic, or geographic characteristics of a particular area.[5]
- Smoke screening - the practice of creating clouds of smoke positioned to provide concealment, allowing military forces to advance or retreat across open terrain without coming under direct fire from the enemy .[6]
Small unit

The use of suppressive fire is a key part of modern small unit tactics
- Individual movement techniques
- Fire and movement (also known as leapfrogging) – working in 'fire teams', one team attempts to suppress the enemy while the other moves either toward the enemy or to a more favourable position.
- Basic drill – a standard drill that all individual soldiers are supposed to perform if they come under fire.
- Contact drill
- Immediate ambush drill
- Counter ambush drill
- Hull-down (in armored warfare)
- Shoot-and-scoot
- Infiltration tactics
- Marching fire
- Four Fs: find, fix, flank, finish
- Overwatch
- Center peel
- Patrolling
- Reconnaissance patrol
- Fighting patrol
- Standing patrol (OP/LP)
- Ambush
- Linear ambush
- L ambush
- Area ambush
- Guerrilla
- Sniper trap - A sniper trap (colloquial term in US military “Chechen rat trap”) is a tactic used by snipers in which the sniper intentionally shoots to wound instead of kill an enemy combatant, with the end goal of drawing more enemy personnel into the field of fire so the sniper can fire on them as they provide aid to their wounded comrade. Not only does this tactic provide more targets for the sniper as enemy personnel come to help the wounded, but it also causes the sniper’s enemy to expend more resources in recovering, evacuating, and treating the wounded combatant than would be expended if the sniper simply killed the enemy combatant.
Eight classical maneuvers of warfare
- Penetration of the center: This involves the creation of a gap in the enemy line and its exploitation. Two ways of accomplishing this are separating enemy forces and using a reserve to exploit the gap that forms between them (e.g. Battle of Chaeronea (338 BC), the first recorded use of the penetration of the center) or having fast, elite forces smash at a specific point in the enemy line (an enemy weak spot or an area where your elites are at their best in striking power) and, while reserves and holding forces hold your opponent, drive quickly and immediately for the enemy's command or base (i.e., blitzkrieg).
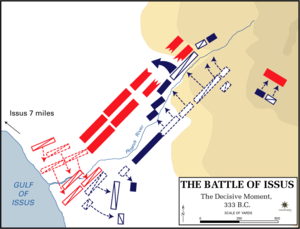 Battle of Issus, a classic example of the single envelopment
Battle of Issus, a classic example of the single envelopment - Attack from a defensive position: Establishing a strong defensive position from which to defend and attack your opponent (e.g., Siege of Alesia and the Battle of the Granicus). However, the defensive can become too passive and result in ultimate defeat.
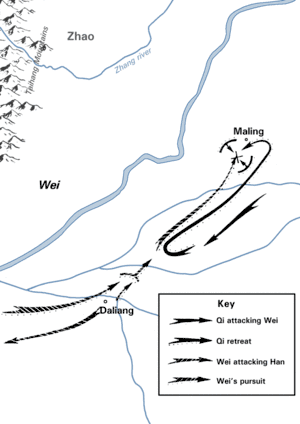 Battle of Maling, the earliest known use of the feigned retreat
Battle of Maling, the earliest known use of the feigned retreat - Single envelopment: A strong flank beating its opponent opposite and, with the aid of holding attacks, attack an opponent in the rear. Sometimes, the establishment of a strong, hidden force behind a weak flank will prevent your opponent from carrying out their own single envelopment (e.g., Battle of Rocroi).
- Double envelopment: Both flanks defeat their opponent opposite and launch a rear attack on the enemy center. Its most famous use was Hannibal's tactical masterpiece, the Battle of Cannae and was frequently used by the Wehrmacht on the Eastern Front of World War II.
- Attack in oblique order: This involves placing your flanks in a slanted fashion (refusing one's flank) or giving a vast part of your force to a single flank (e.g., Battle of Leuthen). The latter can be disastrous, however, due to the imbalance of force.
- Feigned retreat: Having a frontal force fake a retreat, drawing the opponent in pursuit and then launching an assault with strong force held in reserve (such as the Battle of Maling and the Battle of Hastings). However, a feigned retreat may devolve into a real one, such as in the Battle of Grunwald.
- Indirect approach: Having a minority of your force demonstrate in front of your opponent while the majority of your force advance from a hidden area and attack the enemy in the rear or flank (e.g., Battle of Chancellorsville).
- Crossing the "T": a classic naval maneuver which maximizes one side's offensive firepower while minimizing that of the opposing force.
Offensive

The cavalry charge is a quintessential offensive military tactic
- Charge
- Ambush
- Skirmish
- Trench raiding
- Peaceful penetration
- Rapid dominance
- Blitzkrieg – a method of warfare whereby an attacking force is spearheaded by a dense concentration of armoured and motorized or mechanized infantry formations, and heavily backed up by close air support.[7]
- Carpet bombing – also known as saturation bombing, is a large aerial bombing done in a progressive manner to inflict damage in every part of a selected area of land.[8]
- Human wave attack
- Shock tactics
- Swarming (military)
- Planned attack
- Use of supporting fire
- Ambush
- Indirect fire support
- Base of fire
- Flying wedge (used by Alexander the Great)
- Armoured spearhead
- Encirclement
- Hammer and anvil
- Inverted wedge
- Frontal assault
- Holding attack – to hold the enemy in position while other offensive or defensive activity takes place .
- Penetration or infiltration
- Pincer movement – an army assaults an enemy by attacking two sides at opposite locations, often planning to cut off the enemy from retreat or additional support in preparation for annihilation.
- Bull horn formation – an army assaults an enemy force by sending troops to the enemy's flanks and by attacking their front attacking three areas at once, often planning to cut off any retreat or support as well as confusing the enemy in preparation for annihilation.
- Flanking maneuver
- Defeat in detail
- Interdiction – severing or disrupting lines of communication and supply
- Control MSR (main supply routes)
- Envelopment
- Circumvallation
- Finnish motti tactics
- Siege (For attacking fortified places)
- Vertical envelopment
- Airborne forces
- Air mobile forces
- Rapid deployment
- Capturing key points
- Airborne operations
- Air mobile operations
- Amphibious operations
- Motorized operations
- Tank desant
- Mechanized operations
- Armored operations
- Raiding – a small team is inserted deep behind enemy lines to capture a high-value individual or destroy a vital enemy installation then extracted before the enemy can respond.
- Decapitation strike
- Preemptive war
- Disrupting communications
- Electronic countermeasures
- Radar jamming
- Radio jamming
Defensive

Defensive trenches were used commonly during World War I
- Basic principles
- Defence in depth
- Mutual support (e.g., by crossfire)
- Echelon formation
- Phalanx formation
- All round defence
- Force dispersal
- Fire Trap
- Fighting withdrawal
- Reserved demolitions
- Scorched earth
- Booby traps
- Trench warfare
- Counter attack
- Breakout
- Counter battery fire
- Rapid reaction force
- Delaying defence
- Break contact
- Hedgehog defence
- military bottleneck
- Pakfront
- Fortification
- Field works (entrenchments)
- Over head protection
- Revetting
- Sangars
- Shell scrapes
- Foxholes
- Manholes
- Spider holes
- Strongpoints
- Field works (entrenchments)
- Use and improvement of terrain
- High ground
- Protection
- Natural barriers – e.g., rivers
- Reverse slope defence
- Obstacles and barriers – man made
- Barbed wire
- Anti-vehicle ditches
- Anti-vehicle berms (knife edges)
- Multiple axis of movement
Deception
A mounted archer of the Ming Dynasty Army fires a parthian shot
- Deception and misdirection
- Deception: Sun Tzu said that all war is based on deception back in the 4th century BC; a wise commander takes measures to let his opponent only react to the wrong circumstances. Diversionary attacks, feints, decoys; there are thousands of tricks that have been successfully used, and still have a role in the future.
- Perfidy: Combatants tend to have assumptions and ideas of rules and fair practices in combat, but the ones who raise surrender flags to lure their attackers in the open, or who act as stretcher bearers to deceive their targets, tend to be especially disliked.
- False flag: An ancient ruse de guerre – in the days of sail, it was permissible for a warship to fly the flag of an enemy power, so long as it properly hoisted its true colors before attacking. Wearing enemy uniforms and using enemy equipment to infiltrate or achieve surprise is also permissible though they can be punished as spies if caught behind enemy lines.
- Demoralization (warfare): A process in psychological warfare that can encourage them to retreat, surrender, or defect rather than defeating them in combat.
- Disinformation
- Military camouflage
- Stealth technology
- Feint or diversionary attacks
- Electronic warfare
- Electronic countermeasures
- Electronic counter-countermeasures
- Radio silence – while traveling, a fleet will refrain from communicating by radio to avoid detection by enemy forces.
- Force multiplication
- Deception: Sun Tzu said that all war is based on deception back in the 4th century BC; a wise commander takes measures to let his opponent only react to the wrong circumstances. Diversionary attacks, feints, decoys; there are thousands of tricks that have been successfully used, and still have a role in the future.
- Use of surprise
gollark: Cannot reproduce.
gollark: Spatial IO is basically for moving areas of space in and out of the world at the cost of significant amounts of RF.
gollark: Plus I plan to use the spatial IO frame to include useful stuff like a garden.
gollark: Er, if you count the water in that tank, there is one.
gollark: Compact machine with integrated spatial IO frame.
See also
References
- Bretnor, Reginald (February 1, 2001). Decisive Warfare: A Study in Military Theory (New ed.). Wildside Press. pp. 49–52. ISBN 9781587152481. Retrieved December 10, 2016.
- Doughty, Robert. "Weather in War". The History Channel. Archived from the original on 13 October 2013. Retrieved 13 December 2013.
- "SOME JUICY QUOTES FROM CLAUSEWITZ, ON WAR". The Clausewitz Homepage. Retrieved December 13, 2013.
- Toppe, Alfred. Night Combat. Google books. Retrieved December 13, 2013.
- Field Manual (FM) 7–92: The Infantry Reconnaissance Platoon and Squad (Airborne, Air Assault, Light Infantry). United States Army. 2001. p. 40.
- "Definition of SMOKE SCREEN". www.merriam-webster.com. Retrieved 2019-05-29.
- Glantz 2010, Preface
- Gooderson, Ian (1997). Air Power at the Battlefront: Allied Close Air Support in Europe, 1943–45 (1. publ. ed.). London: F. Cass. p. 129. ISBN 0-7146-4680-6.
External links
This article is issued from Wikipedia. The text is licensed under Creative Commons - Attribution - Sharealike. Additional terms may apply for the media files.