Radical 25
Radical 25 meaning "divination" is 1 of 23 Kangxi radicals (214 radicals total) composed of two strokes.
| 卜 | ||
|---|---|---|
| ||
| 卜 (U+535C) "divination" | ||
| Pinyin: | bǔ | |
| Bopomofo: | ㄅㄨˇ | |
| Wade–Giles: | pu3 | |
| Cantonese Yale: | būk | |
| Jyutping: | buk1 | |
| Pe̍h-ōe-jī: | poh (col.) pok (lit.) | |
| Kana: | ホク hoku うらなう uranau | |
| Kanji: | 卜の卜 bokunoto | |
| Hangul: | 점 cheom | |
| Sino-Korean: | 복 bok | |
| Stroke order animation | ||
 | ||
In the Kangxi Dictionary, there are 45 characters (out of 49,030) to be found under this radical.
Characters with Radical 25
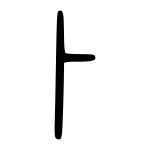
Small seal script character
| strokes | character |
|---|---|
| without additional strokes | 卜 ⺊ |
| 2 additional strokes | 卝 卞 |
| 3 additional strokes | 卟 占 卡 卢 |
| 5 additional strokes | 卣 卤 |
| 6 additional strokes | 卥 卦 |
| 7 additional strokes | 卧 |
| 9 additional strokes | 卨 |
Literature
- Fazzioli, Edoardo (1987). Chinese calligraphy : from pictograph to ideogram : the history of 214 essential Chinese/Japanese characters. calligraphy by Rebecca Hon Ko. New York, 1987: Abbeville Press. ISBN 0-89659-774-1.CS1 maint: location (link)
- Lunde, Ken (Jan 5, 2009). "Appendix J: Japanese Character Sets" (PDF). CJKV Information Processing: Chinese, Japanese, Korean & Vietnamese Computing (Second ed.). Sebastopol, Calif.: O'Reilly Media. ISBN 978-0-596-51447-1.
gollark: I think modern WiFi stuff uses *multiple* antennas, actually, it's called "MIMO".
gollark: It would also not be very useful for spying on people, since they would just stop saying things if they got a notification saying "interception agent has been added to the chat" and it wouldn't work retroactively.
gollark: One proposal for backdooring encrypted messaging stuff was to have a way to remotely add extra participants invisibly to an E2Ed conversation. If you have that but without the "invisible" bit, that would work as "encryption with a backdoor, but then make it very obvious that the backdoor has been used" somewhat.
gollark: Not encryption itself, probably.
gollark: They don't seem to want to *ban* end-to-end encryption as much as backdoor the popularly used stuff. Which is still bad. I should finish writing that blog post on it some time this decade.
This article is issued from Wikipedia. The text is licensed under Creative Commons - Attribution - Sharealike. Additional terms may apply for the media files.