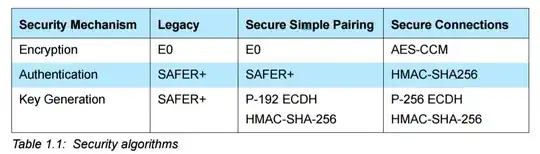
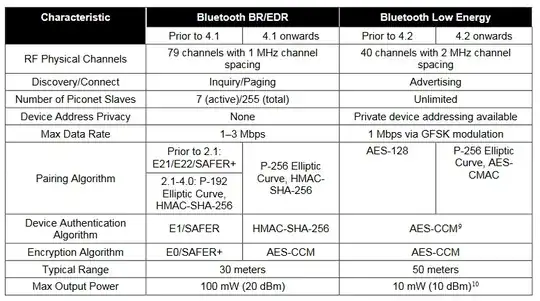
From another question in SO, I got to know a lot about authentication, key generation and encryption algorithms available in Bluetooth BR/EDR:
I also read the official specification, and it says that LE Secure Connections and BR/EDR Secure Connections are functionally equal. However, I didn't manage to find a word about what algorithms are used in Bluetooth Secure Simple Pairing LE for authentication, key generation and encryption. I dig through the docs, but I didn't find the answer.
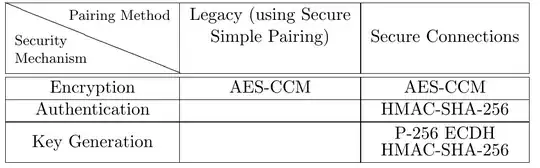
I found somewhere online that SSP in LE uses AES-CCM for encryption (is it true for sure?), so the analogous table for Bluetooth LE should look like the one below, right?