I would like to know what are the differences between Secure Simple Pairing and Secure Connections in Bluetooth v4.2.
Between BR/EDR legacy, BR/EDR, LE, LE legacy, I don't get it.
I would like to know what are the differences between Secure Simple Pairing and Secure Connections in Bluetooth v4.2.
Between BR/EDR legacy, BR/EDR, LE, LE legacy, I don't get it.
Most answers to your questions are given in the spec Bluetooth Core, VOL1.PartA.5
The following suites exist:
BR/EDR
LE
It all started with the initial security algorithms (BR/EDR legacy) for the following security features:
The algorithms used in BR/EDR legacy were not FIPS approved.
This was introduced in version 2.1. Secure Simple Pairing uses FIPS-approved algorithms for pairing and message integrity and so in essence it upgraded the security of BR/EDR legacy, which is why we call this new one BR/EDR security.
Version 4.0 ported the exact same security model as BR/EDR to Low Energy (LE), with the following exceptions:
In version 4.1, the Secure Connections feature was added to BR/EDR. This was an upgrade to the existing Secure Simple Pairing algorithms for pairing, device authentication, and message integrity. See table for a comparison with the Simple Pairing method for BR/EDR (not LE!):
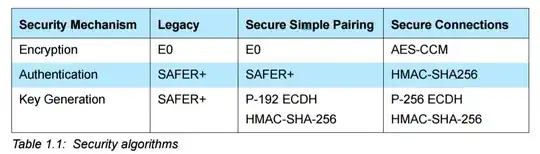
Version 4.2 then upgraded LE as well. One of the main improvements was the adoption of ECDH for pairing. It also modified the Numeric Comparison association model to be used on Bluetooth LE. LE pairing used in 4.0 and 4.1 is since then referred to as LE Legacy. LE Secure Connections and BR/EDR Secure Connections are functionally equal.