Your specific keyboard uses two-level E0 for encryption and P-192 for key exchange.
Bluetooth always uses encryption. However, the different versions use different encryption protocols:
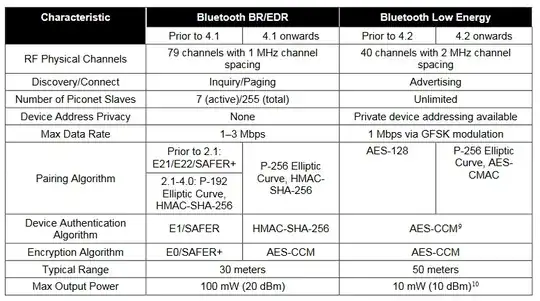
So, what cryptography does each version use? For Bluetooth BR/EDR:
Prior to 2.1, versions do not use any key exchange. Keys are pre-shared, usually using a very weak PIN. They are often vulnerable to brute force as a result of the small keyspace. The cipher is E0, which is fairly weak and can be broken with a known plaintext attack given enough data.
From 2.1 to 4.0, key exchange is performed with ECC, specifically the NIST P-192 curve. This provides approximately 96 bits of classical security which isn't great, but isn't practical to break yet. Although it uses the rather weak E0 cipher, it uses so-called two-level E0, which is a more secure construction that uses the cipher twice. No practical attacks are known against it the way it is used in Bluetooth, but attacks only get better, not worse, so the cipher should be considered weak.
Since 4.1, key exchange is performed using a much stronger ECC curve, P-256, which gives approximately 128 bits of classical security. The cipher used, AES, is also superior to E0. These versions of Bluetooth are generally immune to passive attacks. Active MITM attacks may be possible if out-of-band authentication is not used and a weak PIN is used for authentication instead.
Bluetooth Low Energy (LE) is a little different and was only supported since 4.0. Prior to version 4.2, Bluetooth LE does not use any key exchange mechanism, making it vulnerable to passive attacks. This is a severe regression and can only be mitigated by using BR/EDR instead of LE, or by ensuring only LE version 4.2 or newer (which re-introduced P-256 for key exchange) is used.
According to a quick web search, the Celicious Tri BK01 Bluetooth keyboard uses version 3.0, which means it is using P-192 for key exchange and two-level E0 for encryption. No practical cryptographic attacks are known that can be used against this keyboard, but weaknesses in E0's design and the only barely adequate security of P-192 mean that advances in cryptanalysis in the near future may render it vulnerable. Do not use it in situations where long-term security is required.
Now, your real question shouldn't be what kind of encryption is being used, but how secure it is for entering passwords or other sensitive information. Excluding EMSEC (TEMPEST-type) issues, timing attacks may be possible. Each time you press a key, the keyboard immediately transmits it wirelessly. Although the key press may be encrypted, the fact that a key has been pressed and the exact time it was pressed (and released) is not hidden. It is possible to deduce potential passwords simply by viewing timing patterns, as certain sequences of key presses occur with different timing patterns than others. This problem becomes bigger the more often you enter your password. If your adversary may be collecting both the encrypted data as well as the precise timing intervals of the transmissions, your password may be revealed if entered enough times.
Related:
