Unikernel
A unikernel is a specialised, single address space machine image constructed by using library operating systems.[1][2] A developer selects, from a modular stack, the minimal set of libraries which correspond to the OS constructs required for their application to run. These libraries are then compiled with the application and configuration code to build sealed, fixed-purpose images (unikernels) which run directly on a hypervisor or hardware without an intervening OS such as Linux or Windows.
The first such systems were Exokernel and Nemesis in the late 1990s.
Design
In a library operating system, protection boundaries are pushed to the lowest hardware layers, resulting in:
- a set of libraries that implement mechanisms such as those needed to drive hardware or talk network protocols;
- a set of policies that enforce access control and isolation in the application layer.
The library OS architecture has several advantages and disadvantages compared with conventional OS designs. One of the advantages is that since there is only a single address space, there is no need for repeated privilege transitions to move data between user space and kernel space. Therefore, a library OS can provide improved performance by allowing direct access to hardware without having to transition between user mode and kernel mode (on a traditional kernel this transition consists of a single TRAP instruction[3] and is not the same as a context switch[4]). Performance gains may be realised by elimination of the need to copy data between user space and kernel space, although this is also possible with Zero-copy device drivers in traditional operating systems.
A disadvantage is that because there is no separation, trying to run multiple applications side by side in a library OS, but with strong resource isolation, can become complex.[5] In addition, device drivers are required for the specific hardware the library OS runs on. Since hardware is rapidly changing this creates the burden of regularly rewriting drivers to remain up to date.
OS virtualization can overcome some of these drawbacks on commodity hardware. A modern hypervisor provides virtual machines with CPU time and strongly isolated virtual devices. A library OS running as a virtual machine only needs to implement drivers for these stable virtual hardware devices and can depend on the hypervisor to drive the real physical hardware. However, protocol libraries are still needed to replace the services of a traditional operating system. Creating these protocol libraries is where the bulk of the work lies when implementing a modern library OS.[1] Additionally, reliance on a hypervisor may reintroduce performance overheads when switching between the unikernel and hypervisor, and when passing data to and from hypervisor virtual devices.
By reducing the amount of code deployed, unikernels necessarily reduce the likely attack surface and therefore have improved security properties.[6][7]
Unikernels have been shown to be around 4% the size of the equivalent code bases using a traditional OS.[8]
Due to the nature of their construction, it is possible to perform whole-system optimisation across device drivers and application logic, thus improving on the specialisation.[9][10]
Unikernels have been regularly shown to boot extremely quickly, in time to respond to incoming requests before the requests time-out.[11][12][13]
Unikernels lend themselves to creating systems that follow the service-oriented or microservices software architectures.
The high degree of specialisation means that unikernels are unsuitable for the kind of general purpose, multi-user computing that traditional operating systems are used for. Adding additional functionality or altering a compiled unikernel is generally not possible and instead the approach is to compile and deploy a new unikernel with the desired changes.
Examples
There are a number of new approaches to constructing unikernels, which are at varying degrees of maturity.
- ClickOS[10][14] is a high-performance, virtualized software middle box platform based on open source virtualization. Early performance analysis shows that ClickOS VMs are small (5MB), boot quickly (as little as 20 milliseconds), add little delay (45 microseconds) and more than 100 can be concurrently run while saturating a 10Gb pipe on an inexpensive commodity server.
- Clive[15] is an operating system designed to work in distributed and cloud computing environments, written in the Go programming language.
- Drawbridge is a research prototype of a new form of virtualization for application sandboxing. Drawbridge combines two core technologies: a picoprocess, which is a process-based isolation container with a minimal kernel API surface, and a library OS, which is a version of Windows enlightened to run efficiently within a picoprocess.[16]
- Graphene Library OS[5][17] is a Linux-compatible library operating system that focuses on securing multi-process, server-type or shell-type legacy applications. Graphene spans a multi-process application across multiple picoprocesses, with inter-process abstractions (e.g., signals, message queues, semaphores) coordinated over simple pipe-like streams. For applications with multiple security principles, Graphene can dynamically sandbox an insecure picoprocess.
- The Haskell Lightweight Virtual Machine (HaLVM) is a port of the Glasgow Haskell Compiler tool suite that enables developers to write high-level, lightweight VMs that can run directly on the Xen hypervisor.
- HermitCore[18] is a novel unikernel targeting a scalable and predictable runtime behavior for HPC and cloud environments. HermitCore supports C, C++, Fortran, Go, Pthreads, OpenMP and iRCCE[19] as message passing library. It is a research project that extends the multi-kernel approach and combines it with unikernel features. HermitCore can directly run on the KVM hypervisor but also on natively on x86_64 architecture.
- HermiTux[20] is an evolution of HermitCore and is a research project aiming to run as unikernels unmodified Linux application binaries.
- IncludeOS is a minimal, service oriented, open source, includable library operating system for cloud services. It's designed for running C++ code on virtual hardware.
- LING[21] is a unikernel based on the Erlang/OTP and understands .beam files. Developers can create code in Erlang and deploy it as LING unikernels. LING removes the majority of vector files, uses only three external libraries and no OpenSSL.
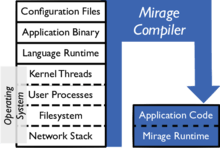
- MirageOS[22] is a clean-slate library operating system that constructs unikernels for secure, high-performance network applications across a variety of cloud computing and mobile platforms. There are now more than 100 MirageOS libraries[23] and a growing number of compatible libraries within the wider OCaml ecosystem.
- OSv is a new OS designed specifically for cloud VMs from Cloudius Systems.[24] Able to boot in less than a second, OSv is designed from the ground up to execute a single application on top of any hypervisor, resulting in superior performance, speed and effortless management. OSv can run unmodified Linux executables (with some limitations), and support for C, C++, JVM, Ruby and Node.js application stacks is available.
- Rumprun is a software stack which enables running existing unmodified POSIX software as a unikernel. Rumprun supports multiple platforms, from bare ARM hardware to hypervisors such as Xen. It is based on the NetBSD rump kernel which provide free, portable, componentized, kernel quality drivers such as file systems, POSIX system call handlers, PCI device drivers, a SCSI protocol stack, virtio and a TCP/IP stack.[25]
- Runtime.js is an open-source library operating system for the cloud that runs on JavaScript VM, could be bundled up with an application and deployed as a lightweight and immutable VM image. Runtime.js is built on the V8 Javascript engine and currently supports QEMU/KVM hypervisor.
- Nanos is a unikernel that runs on QEMU/KVM and Xen hypervisors. It can load arbitrary ELF binaries and is implemented by the builder/orchestrator "OPS".
- TamaGo is a framework that enables compilation and execution of unencumbered Go applications on bare metal ARM SoC based boards, supporting creation of Go unikernels without any direct or indirect dependency on other components or programming languages.
- Unikraft: The high-level goal of Unikraft is to be able to build unikernels targeted at specific applications without requiring the time-consuming, expert work that building such a unikernel requires today. An additional goal (or hope) of Unikraft is that all developers interested in unikernel development would contribute by supplying libraries rather than working on independent projects with different code bases as it is done now.
See also
- Microkernel
- Container (virtualization)
- Rump kernel
References
- "Unikernels: Rise of the Virtual Library Operating System". Retrieved 31 August 2015.
- "Unikernel.org". Unikernel.org. Retrieved 1 December 2015.
- Tanenbaum, Andrew S. (2008). Modern Operating Systems (3rd ed.). Prentice Hall. pp. 50–51. ISBN 978-0-13-600663-3.
. . . nearly all system calls [are] invoked from C programs by calling a library procedure . . . The library procedure . . . executes a TRAP instruction to switch from user mode to kernel mode and start execution . . .
- Context switch#User and kernel mode switching
- Chia-Che, Tsai; Arora, Kumar-Saurabh; Bandi, Nehal; Jain, Bhushan; Jannen, William; John, Jitin; Kalodner, Harry; Kulkarni, Vrushali; Oliviera, Daniela; Porter, Donald E. (2014). Cooperation and Security Isolation of Library OSes for Multi-process Applications (PDF). Proceedings of the Ninth European Conference on Computer Systems (EuroSys). pp. 1–14. CiteSeerX 10.1.1.589.1837. doi:10.1145/2592798.2592812. ISBN 9781450327046.
- "Why Unikernels Can Improve Internet Security". April 2015. Retrieved 31 August 2015.
- Madhavapeddy, Anil; Mortier, Richard; Charalampos, Rotsos; Scott, David; Singh, Balraj; Gazagnaire, Thomas; Smith, Steven; Hand, Steven; Crowcroft, Jon (March 2013). "Unikernels: Library Operating Systems for the Cloud" (PDF). SIGPLAN Notices (ASPLOS 13). 48 (4): 461. doi:10.1145/2499368.2451167.
- Kaloper-Meršinjak, David; Mehnert, Hannes; Madhavapeddy, Anil; Sewell, Peter (2015). "Not-Quite-So-Broken TLS: Lessons in Re-Engineering a Security Protocol Specification and Implementation". Proceedings of the 24th USENIX Security Symposium (USENIX Security 15).
- Madhavapeddy, Anil; Mortier, Richard; Sohan, Ripduman; Gazagnaire, Thomas; Hand, Steven; Deegan, Tim; McAuley, Derek; Crowcroft, Jon (2010). "Turning Down the LAMP: Software Specialisation for the Cloud" (PDF). Proceedings of the 2Nd USENIX Conference on Hot Topics in Cloud Computing.
- Martins, Joao; Mohamed, Ahmed; Raiciu, Costin; Huici, Felipe (2013). Enabling Fast, Dynamic Networking Processing with ClickOS (PDF). Proceedings of the Second ACM SIGCOMM Workshop on Hot Topics in Software Defined Networking. p. 67. doi:10.1145/2491185.2491195. ISBN 9781450321785.
- "Just-in-Time Summoning of Unikernels (v0.2)". Magnus Skjegstad. Retrieved 30 August 2015.
- "Zerg". Zerg — an instance per request demo. Retrieved 30 August 2015.
- Madhavapeddy, Anil; Leonard, Thomas; Skjegstad, Magnus; Gazagnaire, Thomas; Sheets, David; Scott, David; Mortier, Richard; Chaudhry, Amir; Singh, Balraj; Ludlam, Jon; Crowcroft, Jon; Leslie, Ian (2015). Jitsu: Just-In-Time Summoning of Unikernels (PDF). The 12th USENIX Conference on Networked Systems Design and Implementation (NSDI). ISBN 978-1-931971-218.
- "ClickOS and the Art of Network Function Virtualization" (PDF). Retrieved 31 August 2015.
- "The Clive Operating System" (PDF). Retrieved 31 August 2015.
- "Drawbridge". Microsoft Research. Retrieved 30 August 2015.
- "Graphene library OS". Stony Brook University. Retrieved 31 Jan 2016.
- "HermitCore – A Unikernel for Extreme-Scale Computing". Retrieved 8 June 2016.
- "iRCCE: A Non-blocking Communication Extension to the RCCE Communication Library for the Intel Single-Chip Cloud Computer" (PDF). Retrieved 8 June 2016.
- Olivier, Pierre; Chiba, Daniel; Lankes, Stefan; Min, Changwoo; Ravindran, Binoy (2019). "A binary-compatible unikernel". Proceedings of the 15th ACM SIGPLAN/SIGOPS International Conference on Virtual Execution Environments - VEE 2019. New York, New York, USA: ACM Press: 59–73. doi:10.1145/3313808.3313817. ISBN 978-1-4503-6020-3.
- "Erlang on Xen: at the heart of super-elastic clouds". Retrieved 31 August 2015.
- "MirageOS: A programming framework for building type-safe, modular systems". Retrieved 31 August 2015.
- "MirageOS TROVE". Retrieved 31 August 2015.
- Kivity, Avi; Costa, Glauber; Enberg, Pekka; Har'El, Nadav; Marti, Don; Zolotarov, Vlad (June 2014). "OSv: Optimizing the Operating System for Virtual Machines" (PDF). 2014 USENIX Annual Technical Conference.
- "Rump Kernels". rumpkernel.org. Retrieved 31 August 2015.