Cloud storage
Cloud storage is a model of computer data storage in which the digital data is stored in logical pools, said to be on "the cloud". The physical storage spans multiple servers (sometimes in multiple locations), and the physical environment is typically owned and managed by a hosting company. These cloud storage providers are responsible for keeping the data available and accessible, and the physical environment protected and running. People and organizations buy or lease storage capacity from the providers to store user, organization, or application data.
Cloud storage services may be accessed through a colocated cloud computing service, a web service application programming interface (API) or by applications that utilize the API, such as cloud desktop storage, a cloud storage gateway or Web-based content management systems.
History
Cloud computing is believed to have been invented by Joseph Carl Robnett Licklider in the 1960s with his work on ARPANET to connect people and data from anywhere at any time.[1]
In 1983, CompuServe offered its consumer users a small amount of disk space that could be used to store any files they chose to upload.[2]
In 1994, AT&T launched PersonaLink Services, an online platform for personal and business communication and entrepreneurship. The storage was one of the first to be all web-based, and referenced in their commercials as, "you can think of our electronic meeting place as the cloud."[3] Amazon Web Services introduced their cloud storage service AWS S3 in 2006, and has gained widespread recognition and adoption as the storage supplier to popular services such as SmugMug, Dropbox, and Pinterest. In 2005, Box announced an online file sharing and personal cloud content management service for businesses.[4]
Architecture
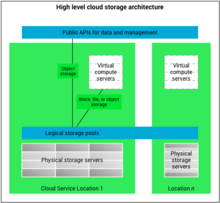
Cloud storage is based on highly virtualized infrastructure and is like broader cloud computing in terms of accessible interfaces, near-instant elasticity and scalability, multi-tenancy, and metered resources. Cloud storage services can be utilized from an off-premises service (Amazon S3) or deployed on-premises (ViON Capacity Services).[5]
Cloud storage typically refers to a hosted object storage service, but the term has broadened to include other types of data storage that are now available as a service, like block storage.
Object storage services like Amazon S3, Oracle Cloud Storage and Microsoft Azure Storage, object storage software like Openstack Swift, object storage systems like EMC Atmos, EMC ECS and Hitachi Content Platform, and distributed storage research projects like OceanStore[6] and VISION Cloud[7] are all examples of storage that can be hosted and deployed with cloud storage characteristics.
Cloud storage is:[6]
- Made up of many distributed resources, but still acts as one, either in a federated[8] or a cooperative storage cloud architecture
- Highly fault tolerant through redundancy and distribution of data
- Highly durable through the creation of versioned copies
- Typically eventually consistent with regard to data replicas[9]
Advantages
- Companies need only pay for the storage they actually use, typically an average of consumption during a month.[10] This does not mean that cloud storage is less expensive, only that it incurs operating expenses rather than capital expenses.
- Businesses using cloud storage can cut their energy consumption by up to 70% making them a more green business.[11]
- Organizations can choose between off-premises and on-premises cloud storage options, or a mixture of the two options, depending on relevant decision criteria that is complementary to initial direct cost savings potential; for instance, continuity of operations (COOP), disaster recovery (DR), security (PII, HIPAA, SARBOX, IA/CND), and records retention laws, regulations, and policies.[12]
- Storage availability and data protection is intrinsic to object storage architecture, so depending on the application, the additional technology, effort and cost to add availability and protection can be eliminated.[13]
- Storage maintenance tasks, such as purchasing additional storage capacity, are offloaded to the responsibility of a service provider.[10]
- Cloud storage provides users with immediate access to a broad range of resources and applications hosted in the infrastructure of another organization via a web service interface.[14]
- Cloud storage can be used for copying virtual machine images from the cloud to on-premises locations or to import a virtual machine image from an on-premises location to the cloud image library. In addition, cloud storage can be used to move virtual machine images between user accounts or between data centers.[15]
- Cloud storage can be used as natural disaster proof backup, as normally there are 2 or 3 different backup servers located in different places around the globe.
- Cloud storage can be mapped as a local drive with the WebDAV protocol. It can function as a central file server for organizations with multiple office locations.
Potential concerns
Data security
Outsourcing data storage increases the attack surface area.[16]
- When data has been distributed it is stored at more locations increasing the risk of unauthorized physical access to the data. For example, in cloud based architecture, data is replicated and moved frequently so the risk of unauthorized data recovery increases dramatically. Such as in the case of disposal of old equipment, reuse of drives, reallocation of storage space. The manner that data is replicated depends on the service level a customer chooses and on the service provided. When encryption is in place it can ensure confidentiality. Crypto-shredding can be used when disposing of data (on a disk).
- The number of people with access to the data who could be compromised (e.g., bribed, or coerced) increases dramatically. A single company might have a small team of administrators, network engineers, and technicians, but a cloud storage company will have many customers and thousands of servers, therefore a much larger team of technical staff with physical and electronic access to almost all of the data at the entire facility or perhaps the entire company.[17] Decryption keys that are kept by the service user, as opposed to the service provider, limit the access to data by service provider employees. As for sharing multiple data in the cloud with multiple users, a large number of keys has to be distributed to users via secure channels for decryption, also it has to be securely stored and managed by the users in their devices. Storing these keys requires rather expensive secure storage. To overcome that, key-aggregate cryptosystem[18] can be used.
- It increases the number of networks over which the data travels. Instead of just a local area network (LAN) or storage area network (SAN), data stored on a cloud requires a WAN (wide area network) to connect them both.
- By sharing storage and networks with many other users/customers it is possible for other customers to access your data. Sometimes because of erroneous actions, faulty equipment, a bug and sometimes because of criminal intent. This risk applies to all types of storage and not only cloud storage. The risk of having data read during transmission can be mitigated through encryption technology. Encryption in transit protects data as it is being transmitted to and from the cloud service.[19] Encryption at rest protects data that is stored at the service provider. Encrypting data in an on-premises cloud service on-ramp system can provide both kinds of encryption protection.
Longevity
Companies are not permanent and the services and products they provide can change. Outsourcing data storage to another company needs careful investigation and nothing is ever certain. Contracts set in stone can be worthless when a company ceases to exist or its circumstances change. Companies can:[20][21][22]
- Go bankrupt.
- Expand and change their focus.
- Be purchased by other larger companies.
- Be purchased by a company headquartered in or move to a country that negates compliance with export restrictions and thus necessitates a move.
- Suffer an irrecoverable disaster.
Accessibility
- Performance for outsourced storage is likely to be lower than local storage, depending on how much a customer is willing to spend for WAN bandwidth[10]
- Reliability and availability depends on wide area network availability and on the level of precautions taken by the service provider. Reliability should be based on hardware as well as various algorithms used.
- Its a given a multiplicity of data storage.
Other concerns
- Security of stored data and data in transit may be a concern when storing sensitive data at a cloud storage provider[10]
- Users with specific records-keeping requirements, such as public agencies that must retain electronic records according to statute, may encounter complications with using cloud computing and storage. For instance, the U.S. Department of Defense designated the Defense Information Systems Agency (DISA) to maintain a list of records management products that meet all of the records retention, personally identifiable information (PII), and security (Information Assurance; IA) requirements[23]
- Cloud storage is a rich resource for both hackers and national security agencies.[24][25] Because the cloud holds data from many different users and organizations, hackers see it as a very valuable target.[26]
- Piracy and copyright infringement may be enabled by sites that permit filesharing. For example, the CodexCloud ebook storage site has faced litigation from the owners of the intellectual property uploaded and shared there, as have the GrooveShark and YouTube sites it has been compared to.[27][28]
- The legal aspect, from a regulatory compliance standpoint, is of concern when storing files domestically and especially internationally.[29]
Options
There are several options available to avoid such issues. One option is to use a private cloud instead of a public cloud (there are as well providers that offer private cloud storage). Another option is to ingest data in encrypted format where the key is hold within your on premise infrastructure. Access is often by use of cloud storage gateways that are on premise. Such gateways have options not only to encrypt and compress the data prior of transfer but as well mirror the storage across multiple cloud storage providers and remove the risk of a single providers shutdown. Gateways offer as well the option to cache data on a most recently used algorithm on premise. Along with data analytics data is cached and fetched on a most valuable form instead of recently used only form.
See also
References
- "A History of Cloud Computing". ComputerWeekly.
- Louden, Bill (September 1983). "Increase Your 100's Storage with 128K from Compuserve". Portable 100. New England Publications Inc. 1 (1): 22. ISSN 0738-7016.
- Daniela Hernandez (May 23, 2014). "Tech Time Warp of the Week". Wired.
- "Box.net lets you store, share, work in the computing cloud". Silicon Valley Business Journal. December 16, 2009. Retrieved October 2, 2016.
- "On-premises private cloud storage description, characteristics, and options". Archived from the original on 2016-03-22. Retrieved 2012-12-10.
- S. Rhea, C. Wells, P. Eaton, D. Geels, B. Zhao, H. Weatherspoon, and J. Kubiatowicz, Maintenance-Free Global Data Storage. IEEE Internet Computing , Vol 5, No 5, September/October 2001, pp 40–49. Archived 2012-03-29 at the Wayback Machine Archived 2011-06-23 at the Wayback Machine
- Kolodner, Elliot K.; Tal, Sivan; Kyriazis, Dimosthenis; Naor, Dalit; Allalouf, Miriam; Bonelli, Lucia; Brand, Per; Eckert, Albert; Elmroth, Erik; Gogouvitis, Spyridon V.; Harnik, Danny; Hernandez, Francisco; Jaeger, Michael C.; Bayuh Lakew, Ewnetu; Manuel Lopez, Jose; Lorenz, Mirko; Messina, Alberto; Shulman-Peleg, Alexandra; Talyansky, Roman; Voulodimos, Athanasios; Wolfsthal, Yaron (2011). "A Cloud Environment for Data-intensive Storage Services". 2011 IEEE Third International Conference on Cloud Computing Technology and Science: 357–366. CiteSeerX 10.1.1.302.151. doi:10.1109/CloudCom.2011.55. ISBN 978-1-4673-0090-2.
- Vernik, Gil, et al. "Data On-boarding in Federated Storage Clouds." Proceedings of the 2013 IEEE Sixth International Conference on Cloud Computing. IEEE Computer Society, 2013.
- Kemme, Bettina, et al. "Consistency in Distributed Systems (Dagstuhl Seminar 13081)." (2013).
- ZDNet, Nasuni Cloud Storage Gateway By Dan Kusnetzky, June 1, 2010,
- Gupta, P (20 October 2013). "The usage and adoption of cloud computing by small and medium businesses". International Journal of Information Management. 33 (5): 861–874. doi:10.1016/j.ijinfomgt.2013.07.001.
- "Ochs, R. (2012). The New Decision-Makers. CRN (June 22, 2012). Retrieved on December 10, 2012". Archived from the original on August 5, 2016. Retrieved December 10, 2012.
- "4 reasons why cloud and on-premises storage are different, but equally good for people data". 2013-09-09. Archived from the original on 2013-09-25. Retrieved 2013-09-09.
- O’Brien, J. A. & Marakas, G. M. (2011). Computer Software. Management Information Systems 10th ed. 145. McGraw-Hill/Irwin
- Wu C F, Wang Y S, Liu G N, Amies, A, 2012, Create solutions on IBM SmartCloud Enterprise: Transfer image assets between different accounts IBM developerWorks, June 6.
- "The Attack Surface Problem". Sans.edu. Retrieved 2013-07-08.
- Cyber%20 Intrusion%20 Mitigation%20 Strategies .pdf "US-CERT ICS-TIP-12-146-01 Targeted Cyber Intrusion and Detection Mitigation Strategies" Check
|url=value (help) (PDF). - Chu, Cheng-Kang; Chow, Sherman S.M.; Tzeng, Wen-Guey; Zhou, Jianying; Deng, Robert H. (2014-02-01). "Key-Aggregate Cryptosystem for Scalable Data Sharing in Cloud Storage". IEEE Transactions on Parallel and Distributed Systems. 25 (2): 468–477. doi:10.1109/TPDS.2013.112. ISSN 1045-9219.
- Transfer files from one onedrive account to another.
- Butler, Brandon (2 June 2014). "Cloud's worst-case scenario: What to do if your provider goes belly up". Network World. Retrieved 20 June 2015.
- Gaudin, Sharon (12 January 2015). "Verizon gets 'black eye' in long cloud shutdown". ComputerWorld. Retrieved 20 June 2015.
- Butler, Brandon (1 November 2013). "Free cloud storage service MegaCloud goes dark". Network World. Retrieved 20 June 2015.
- "DoDD 5015.2 DOD Records Management Program, Section 5.1.3" (PDF).
- Mello, John P. "National Security Agency Pressed to Reveal Details on Google Deal". PCWorld. Retrieved 2013-07-08.
- Spring, Tom. "Google Ditches Microsoft's Windows Over Security Issues, Report Claims". PCWorld. Retrieved 2013-07-08.
- Subashini, S.; Kavitha, V. (2011-01-01). "A survey on security issues in service delivery models of cloud computing". Journal of Network and Computer Applications. 34 (1): 1–11. doi:10.1016/j.jnca.2010.07.006.
- Justin Pot (7 December 2011). "Codex Cloud: Upload Your Books & Read Them Online Along With Other People's Uploads". MakeUseOf. Archived from the original on 21 October 2016. Retrieved 12 December 2012.
- Nancy Messieh (18 October 2011). "Publishers beware: Is CodexCloud the Grooveshark for ebooks?". NextWeb.
- Jones, Hadley. "When Online File Storage Gets Legal: Regulatory Compliance". CloudWedge. Retrieved 2014-01-16.