I created a basic test PostgreSQL RDS instance in a VPC that has a single public subnet and that should be available to connect over the public internet. It uses the default security group, which is open for port 5432. When I try to connect, it fails. I must be missing something very straightforward -- but I'm pretty lost on this.
Here're the database settings, note that it's marked as Publicly Accessible:
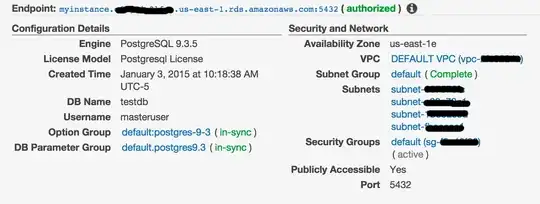
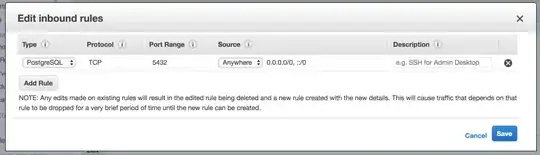
Here're the security group settings, note it's wide open (affirmed in the RDS settings above by the green "authorized" hint next to the endpoint):
Here's the command I'm trying to use to connect:
psql --host=myinstance.xxxxxxxxxx.us-east-1.rds.amazonaws.com \
--port=5432
--username=masteruser
--password
--dbname=testdb
And this is the result I'm getting when trying to connect from a Yosemite MacBook Pro (note, it's resolving to a 54.* ip address):
psql: could not connect to server: Operation timed out
Is the server running on host "myinstance.xxxxxxxxxx.us-east-1.rds.amazonaws.com" (54.xxx.xxx.xxx) and accepting
TCP/IP connections on port 5432?
I do not have any kind of firewall enabled, and am able to connect to public PostgreSQL instances on other providers (e.g. Heroku).
Any troubleshooting tips would be much appreciated, since I'm pretty much at a loss here.
Update
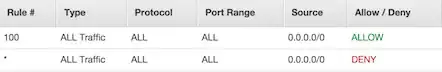
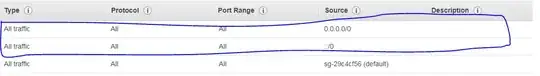
Per comment, here are the inbound ACL rules for the Default VPC: