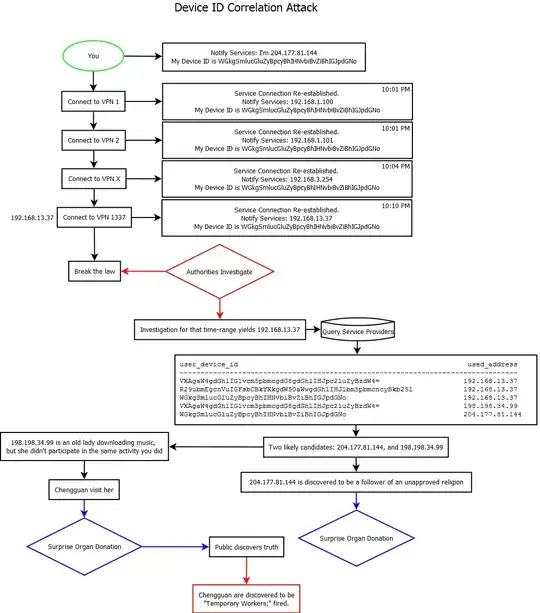
Update/Note: This is not to discourage VPN usage. I personally use one of the providers mentioned below, and I'm very happy with it. The important point is not to have an illusion of being 100% protected by the VPN provider. If you do something bad enough that state actors are after you, the VPN provider aren't going to risk themselves for you. If those coming after you are motivated enough, they'll exert all possible legal (and not so legal) powers they have. Downloading torrents or posting on anarchist forums is probably not motivating enough, but death threats to up-high politicians on the other hand... If there's one thing to take from this post is this: Use common sense.
I've researched this subject for more than 3 years*: Looking for VPN providers, reading through their Privacy Policy and Legal pages, contacting them, contacting their ISPs when possible, and I've concluded the following:
I was able to find zero reputable/trustworthy and publicly-available (free or paid) VPN service provider that:
I'm not exaggerating, absolutely none, zero, nada, nula, nulla, ciphr, cifra.
* Obviously not a dedicated research for 3 years
Update: Regarding "super awesome Swedish VPN service providers". Swedish service provider obey the 'Electronic Communications Act 2003 389'. Sections 5, 6, and 7 under "Processing of traffic data" completely protect your privacy, but go a little further and read section 8
The provisions of Sections 5 to 7 do not apply
When an authority or a court needs access to such data as referred to in Section 5 to resolve disputes.
For electronic messages that are conveyed or have been dispatched or ordered to or from a particular address in an electronic
communications network that is subject to a decision on secret
wire-tapping or secret tele-surveillance.
To the extent data as referred to in Section 5 is necessary to prevent and expose unauthorised use of an electronic communications
network or an electronic communications service.
In case the authorities order secret wire-tapping, the service provider shall not disclose information about it
Section 19 An operation shall be conducted so a decision on secret
wire-tapping and secret tele-surveillance can be implemented and so
that the implementation is not disclosed.
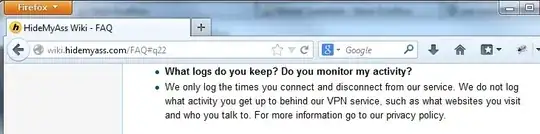
Update 2: Regarding other highly recommended super anonymous VPN services (I'll go over only the top two)
BTGuard: You only need to take one look at the Privacy Policy to know that there's something shady going on.
Before or at the time of collecting personal information, we will identify the purposes for which information is being collected.
We will collect and use of personal information solely with the objective of fulfilling those purposes specified by us and for other
compatible purposes, unless we obtain the consent of the individual
concerned or as required by law.
We will only retain personal information as long as necessary for the fulfillment of those purposes.
We will collect personal information by lawful and fair means and, where appropriate, with the knowledge or consent of the individual
concerned.
You can clearly see the intentionally vague language: "fulfilling those purposes specified by us", what are those purposes specified by them? Nobody knows. They even clearly say that they'll collect personal information when required by the law. In the last point they even state that they even don't have to inform you about the collection of your personal information unless it's "appropriate".
PrivateInternetAccess: This is probably one of the easiest legal language in the business.
You agree to comply with all applicable laws and regulations in
connection with use of this service. You must also agree that you nor
any other user that you have provided access to will not engage in any
of the following activities:
Uploading, possessing, receiving, transporting, or distributing any copyrighted, trademark, or patented content which you do not own or
lack written consent or a license from the copyright owner.
Accessing data, systems or networks including attempts to probe scan or test for vulnerabilities of a system or network or to breach
security or authentication measures without written consent from the
owner of the system or network.
Accessing the service to violate any laws at the local, state and federal level in the United States of America or the country/territory
in which you reside.
If you break any of their conduct conditions (mentioned above)
Failure to comply with the present Terms of Service constitutes a
material breach of the Agreement, and may result in one or more of
these following actions:
- Issuance of a warning;
- Immediate, temporary, or permanent revocation of access to Privateinternetaccess.com with no refund;
- Legal actions against you for reimbursement of any costs incurred via indemnity resulting from a breach;
- Independent legal action by Privateinternetaccess.com as a result of a breach; or
- Disclosure of such information to law enforcement authorities as deemed reasonably necessary.