This is the first time I am using a VPN on my stock Android device. I bought VPN Unlimited mainly because it was on sale and without evaluating competitor products
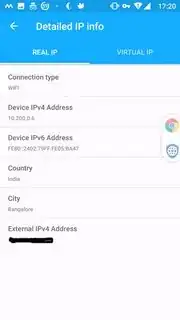
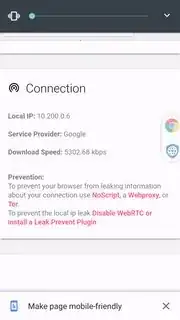
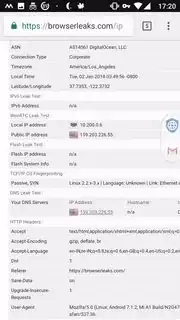
I was playing around with it and it does mask the external IP well on any location I choose. But my concern is with Device IP/Local IP. That does not get masked as you can see from snapshots below (Open VPN Protocol).
This is from the device IP as shown in the app:
These are from webkay and Browser leaks. As you can see Device IP/Local IP are not masked and are clearly visible.
I have read these (and understood at a high level since I am not familiar with VPN security aspects):
- How can you be caught using Private VPN when there's no logs about who you are?
- How can meta data be used to identify users through chained VPNs?
Questions
- Is this expected behavior of VPNs?
- Is it a concern or risk? (The 2nd question above seems to indicate that it is indeed so.)
- Should I be concerned, considering my usage pattern (which is occasional banking, shopping and maybe in the future visiting restricted sites if need be)?
I have written to VPN Unlimited and so far they have not given a clear reply. This makes me more suspicious and hence thought of asking here