This question is inspired by this article (in Russian) about a website called I Know What You Download. From what I understand, they scan the DHT networks and display torrents that any given IP participated in, and although it is sometimes inaccurate, it can provide data on Internet usage, and thus presents a threat to anonymity.
Most people suggest using VPN in order to conceal torrent traffic. However, in another article (also in Russian) same author shares his experience with torrenting over VPN set in Azure. Apparently, he received DMCA notice for torrenting a film (author specifically notes that he did not fully download the film, and everything was done for the sake of experiment). They provided the name and the size of the file, along with IP address and port.
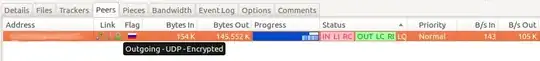
But, some (if not all) torrent-sharing programs have an encryption feature. For instance, Tixati can even enforce encryption for both incoming and outgoing connections:
Question is: what does this feature encrypt? Name of the file, its contents, size? Could it prevent DMCA notices? If not, what does it actually do?
Related: the answer there mentions encryption — does this kind of encryption count?