The initialization vector in WEP is a 24-bit random value that is used to seed the RC4 algorithm.
RC4 is a stream cipher. This means that for each bit of plaintext, it produces one bit of keystream and xors the two, to generate the ciphertext. The keystream is simply a stream of random numbers, generated from the RC4 algorithm.
In the most basic operation of a stream cipher, the algorithm is seeded with a key, such that the same key will always produce the same stream of random numbers. Since both the client and server know the key, they can produce the same keysteam. This allows the client to xor the plaintext with the keystream to produce the ciphertext, and the server to xor the ciphertext with the keystream to produce the plaintext again.
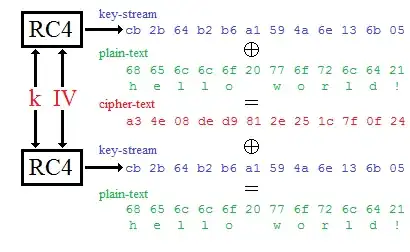
The problem with this is that a key is only a few tens of bits long, but the plaintext may be gigabytes. After a large number of bits have been produced by RC4, the random numbers become predictable, and may even loop back round to the start. This is obviously undesirable, because a known plaintext attack would be able to compute the keystream (c1 xor c2 = k) and use it to decrypt new messages.
In order to solve this problem, an IV was introduced to complement the seed. The IV is a random 24-bit value that changed periodically, in an attempt to prevent re-use of the keystream. Unfortunately, 24 bits is quite small, and the IV often wasn't generated in an unpredictable way, allowing attackers to guess future IVs and use them to deduce the key.
Further attacks involved actively injecting packets into the network, tricking the access point into issuing lots of new IVs, which allowed attackers to crack WEP in minutes or seconds.
Further reading:
