I've been reading a lot about WEP cracking on online resources very recently, however there is one question that no website gives answer to I believe.
I would like to first understand the theory very well.
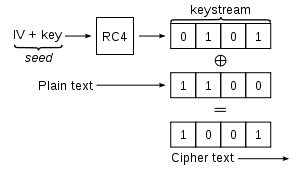
I understand how RC4 stream cipher works:
The IV being very short, with an high enough number of packets (ARP replay attack would be one way to get a lot of packets quickly), it should be possible to get 2 packets with the same IVs. Consequently, the two packets (P1 and P20 would have the same cipher Key (K).
Once you have these 2 packets, you just need to XOR them to obtain such result:
P1 XOR P2 = K XOR M1 XOR K XOR M2 = M1 XOR M2
So, you end up having a XOR of the two clear messages. That makes perfect sense.
However, how can you from there obtain the actual encryption Key ?
I did not find any resource online that would answer this question. They all assume that at that point, when you got a repetition of the IV, you got the key.
Thank you in advance for your help