WinFixer
WinFixer[lower-alpha 1] was a family of scareware rogue security programs developed by Winsoftware which claimed to repair computer system problems on Microsoft Windows computers if a user purchased the full version of the software. The software was mainly installed without the user's consent.[1] McAfee claimed that "the primary function of the free version appears to be to alarm the user into paying for registration, at least partially based on false or erroneous detections."[2] The program prompted the user to purchase a paid copy of the program.[3]
 Screenshot of the WinFixer homepage | |
Type of site | Scareware |
|---|---|
| Available in | English |
| Owner | Innovative Marketing, Inc. |
| Commercial | No |
| Registration | Not required |
| Current status | Shut down by the United States federal government |
Content license | Not protected by copyright laws; see ex turpi causa non oritur actio |
The WinFixer web page (see the image) said it "is a useful utility to scan and fix any system, registry and hard drive errors. It ensures system stability and performance, frees wasted hard-drive space and recovers damaged Word, Excel, music and video files." However, these claims were never verified by any reputable source. In fact, most sources considered this program to actually reduce system stability and performance. The sites went defunct in December 2008 after actions taken by the Federal Trade Commission.
Installation methods
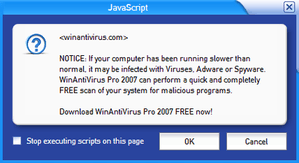
The WinFixer application was known to infect users using the Microsoft Windows operating system, and was browser independent. One infection method involved the Emcodec.E trojan, a fake codec scam. Another involves the use of the Vundo family of trojans.[4]
Typical infection
The infection usually occurred during a visit to a distributing web site using a web browser. A message appeared in a dialog box or popup asking the user if they wanted to install WinFixer, or claimed a user's machine was infected with malware, and requested the user to run a free scan. When the user chose any of the options or tried to close this dialog (by clicking 'OK' or 'Cancel' or by clicking the corner 'X'), it would trigger a pop-up window and WinFixer would download and install itself, regardless of the user's wishes.
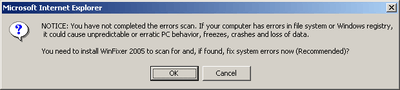
"Trial" offer
A free "trial" offer of this program was sometimes found in pop-ups. If the "trial" version was downloaded and installed, it would execute a "scan" of the local machine and a couple of non-existent trojans and viruses would be "discovered", but no further action would be undertaken by the program. To obtain a quarantine or removal, WinFixer required the purchase of the program.[5] However, the alleged unwanted bugs were bogus, only serving to persuade the owner to buy the program.
WinFixer application
Once installed, WinFixer frequently launched pop-ups and prompted the user to follow its directions. Because of the intricate way in which the program installed itself into the host computer (including making dozens of registry edits), successful removal would have taken a fairly long time if done manually. When running, its process could be found in the task manager and be stopped, but would automatically relaunch itself after a period of time.
WinFixer was also known to modify the Windows Registry so that it started up automatically with every reboot, and scanned the user's computer.[6]
Firefox popup
The Mozilla Firefox browser was vulnerable to initial infection by WinFixer. Once installed, WinFixer was known to exploit the SessionSaver extension for the Firefox browser. The program caused popups on every startup asking the user to download WinFixer, by adding lines containing the word 'WinFixer' to the prefs.js file.
Removal
Removal of WinFixer proved difficult because it actively undid whatever the user attempted. Frequently, procedures that worked on one system would not work on another because there were a large number of variants. Some sites provided manual techniques to remove infections that automated cleanup tools could not remove.[7]
Domain ownership
The company that made WinFixer, Winsoftware Ltd., claimed to be based in Liverpool, England (Stanley Street, postcode: 13088.) However, this address was proven to be false.[8]
The domain WINFIXER.COM on the whois database showed it was owned by a void company in Ukraine and another in Warsaw, Poland.[9] According to Alexa Internet, the domain was owned by Innovative Marketing, Inc., 1876 Hutson St, Honduras.
According to the public key certificate provided by GTE CyberTrust Solutions, Inc., the server secure.errorsafe.com was operated by ErrorSafe Inc. at 1878 Hutson Street, Belize City, BZ.
Running traceroute on Winfixer domains showed that most of the domains were hosted from servers at setupahost.net, which used Shaw Business Solutions AKA Bigpipe as their backbone.
Technical information
Variants
Windows Police Pro
Windows Police Pro was a variant of WinFixer.[11] David Wood wrote in Microsoft TechNet that in March 2009, the Microsoft Malware Protection Center saw ASC Antivirus, the virus' first version. Microsoft did not detect any changes to the virus until the end of July that year when a second variant, Windows Antivirus Pro, appeared. Although multiple new virus versions have since appeared, the virus has been renamed only once, to Windows Police Pro. Microsoft added the virus to its Malicious Software Removal Tool in October 2009.[12]
The virus generated numerous persistent popups and messages displaying false scan reports intended to convince users that their computers were infected with various forms of malware that do not exist. When users attempted to close the popup message, they received confirmation dialog boxes that switched the "Purchase full version" and "Continue evaluating" buttons.[12] Windows Police Pro generated a counterfeit Windows Security Center that warned users about the fake malware.[13]
Bleeping Computer and the syndicated "Propeller Heads" column recommended using Malwarebytes' Anti-Malware to remove Windows Police Pro permanently.[12][14] Microsoft TechNet and Softpedia recommended using Microsoft's Malicious Software Removal Tool to get rid of the malware.[12][15]
Effects on the public
Class action lawsuit
On September 29, 2006, a San Jose woman filed a lawsuit over WinFixer and related "fraudware" in Santa Clara County Superior Court; however, in 2007 the lawsuit was dropped. In the lawsuit, the plaintiffs charged that the WinFixer software "eventually rendered her computer's hard drive unusable. The program infecting her computer also ejected her CD-ROM drive and displayed Virus warnings." [16][17][18]
Ads on Windows Live Messenger
On February 18, 2007, a blog called "Spyware Sucks" reported that the popular instant messaging application Windows Live Messenger had inadvertently promoted WinFixer by displaying a WinFixer advertisement from one of Messenger's ad hosts.[19] A similar occurrence was also reported on some MSN Groups pages. There were other reports before this one (one from Patchou, the creator of Messenger Plus!), and people had contacted Microsoft about the incidents. Whitney Burk from Microsoft issued this problem in his official statement:
Microsoft was notified of malware that was being served through ads placed in Windows Live Messenger banners. As a result of this notification we immediately investigated the reports and removed the offending ads, as this is a violation of our ad serving policy. We can confirm that the ads are no longer being served by any Microsoft system. We apologize for the inconvenience and are reviewing our ad approval process to reduce the chance of an occurrence such as this happening again. To help customers protect their PCs from malware threats, Microsoft recommends customers follow our Protect your PC guidance at www.microsoft.com/protect.
— Whitney Burk, Microsoft
Federal Trade Commission
On December 2, 2008, the Federal Trade Commission requested and received a temporary restraining order against Innovative Marketing, Inc., ByteHosting Internet Services, LLC, and individuals Daniel Sundin, Sam Jain, Marc D’Souza, Kristy Ross, and James Reno, the creators of WinFixer and its sister products. The complaint alleged that the products' advertising, as well as the products themselves, violated United States consumer protection laws.[20] However, Innovative Marketing flouted the court order and was fined $8,000 per day in civil contempt.[21]
On September 24, 2012, Kristy Ross was fined $163 million by the Federal Trade Commission for her part in this.[22][23] The article goes on to say that the WinFixer family of software was simply a con but does not acknowledge that it was in fact a program that made many computers unusable.
Notes
- Also known under various other names, including AVSystemCare, DriveCleaner, ECsecure, ErrorProtector, ErrorSafe, FreePCSecure, Home Antivirus 20xx, PCTurboPro, Performance Optimizer, Personal Antivirus, PrivacyProtector, StorageProtector, SysProtect, SystemDoctor, VirusDoctor, WinAntiSpy, WinAntiSpyware, WinAntiVirusPro, Windows Police Pro, WinReanimator, WinSoftware, WinspywareProtect, XPAntivirus and Your PC Protector.
References
- "Winfixer". F-secure.com. Retrieved 2014-08-14.
- "Computer Virus Attacks, Information, News, Security, Detection and Removal | McAfee". Us.mcafee.com. Retrieved 2014-08-14.
- "WinFixer". Symantec. Retrieved 2014-08-14.
- "How to Remove WinFixer / Virtumonde / Msevents / Trojan.vundo". Bleepingcomputer.com. Retrieved 2014-08-14.
- Vincentas (July 6, 2013). "WinFixer in SpyWareLoop.com". Spyware Loop. Retrieved 2013-07-28.
- Archived November 18, 2007, at the Wayback Machine
- "WinFixer Virus Manual Removal - Vundo Variant". 2006.
- http://castlecops.com/t132998-quot_winfixer_quot_virus_quot_winsoftware_quot_crime_rin.html
- "DNS tools - Manage Monitor Analyze - DNSstuff". www.dnsstuff.com.
- "Vundo". Archived from the original on September 30, 2007. Retrieved February 26, 2006.
- Long, Daniel (2009-10-02). "Fake Antivirus: 5 software titles you should definitely NOT install". PC & Tech Authority. nextmedia. Archived from the original on 2009-10-04. Retrieved 2014-12-02.
- Wood, David (2009-10-13). "Scanti-ly Clad - Another Rogue Stripped by MSRT". Microsoft TechNet. Archived from the original on 2013-01-06. Retrieved 2014-11-13.
- Abrams, Lawrence (2009-09-01). "Remove Windows Police Pro (Removal Guide)". Bleeping Computer. Archived from the original on 2009-09-03. Retrieved 2014-11-15.
- "Getting rid of malware". Coeur d'Alene Press. Propeller Heads. 2009-10-11. Retrieved 2014-11-11.
- Oiaga, Marius (2009-10-15). "Windows Antivirus Pro Tackled by the Microsoft Malicious Software Removal Tool". Softpedia. Archived from the original on 2014-11-11. Retrieved 2014-11-11.
- Jeremy Kirk (March 8, 2007). "Lawyer sleuths out mystery around 'Winfixer'". Computerworld. Retrieved 2014-08-14.
- "Malware victim tries in vain to punish its source - San Jose Mercury News". Mercurynews.com. Retrieved 2014-08-14.
- "Lawsuit Filed Against Winfixer (a/k/a ErrorSafe, WinAntiSpyware, WinAntiVirus, SystemDoctor and DriveCleaner)". The Internet Patrol. Retrieved 2014-08-14.
- Archived July 5, 2008, at the Wayback Machine
- "Court Halts Bogus Computer Scans". Federal Trade Commission (United States). December 10, 2008. Retrieved 2008-12-11.
- "Accused Scareware mongers held in contempt of court". The Register (United Kingdom). December 24, 2008. Retrieved 2008-12-24.
- Ionescu, Daniel (October 3, 2012). "Scareware con artist fined $163 million by FTC". techhive.com. Retrieved 2012-10-03.
- "Winfixer Opinion" (PDF). US Federal Trade Commission. September 24, 2012. Retrieved 2012-10-03.