Pigpen cipher
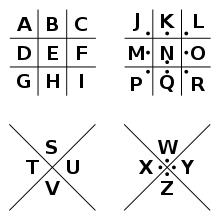
The pigpen cipher (alternatively referred to as the masonic cipher, Freemason's cipher, Napoleon cipher, and tic-tac-toe cipher)[2][3] is a geometric simple substitution cipher, which exchanges letters for symbols which are fragments of a grid. The example key shows one way the letters can be assigned to the grid.
Security
The use of symbols instead of letters is no impediment to cryptanalysis, and this system is identical to that of other simple monoalphabetic substitution schemes. Due to the simplicity of the cipher, it is often included in children's books on ciphers and secret writing.[4]
History
The cipher is believed to be an ancient cipher[5][6] and is said to have originated with the Hebrew rabbis.[7][8] Thompson writes that, “there is evidence that suggests that the Knights Templar utilized a pig-pen cipher” during the Christian Crusades.[9][10]
Parrangan & Parrangan write that it was used by an individual, who may have been a Mason, “in the 16th century to save his personal notes.”[11]
In 1531 Cornelius Agrippa described an early form of the Rosicrucian cipher, which he attributes to an existing Jewish Kabbalistic tradition.[12] This system, called "The Kabbalah of the Nine Chambers" by later authors, used the Hebrew alphabet rather than the Latin alphabet, and was used for religious symbolism rather than for any apparent cryptological purpose.[13]
Variations of this cipher were used by both the Rosicrucian brotherhood[14] and the Freemasons, though the latter used the pigpen cipher so often that the system is frequently called the Freemason's cipher. Hysin claims it was invented by Freemasons.[15] They began using it in the early 18th century to keep their records of history and rites private, and for correspondence between lodge leaders.[3][16][17] Tombstones of Freemasons can also be found which use the system as part of the engravings. One of the earliest stones in Trinity Church Cemetery in New York City, which opened in 1697, contains a cipher of this type which deciphers to "Remember death" (cf. "memento mori").
George Washington's army had documentation about the system, with a much more randomized form of the alphabet. And during the American Civil War, the system was used by Union prisoners in Confederate prisons.[14]
Example
Using the Pigpen cipher key shown in the example above, the message "X MARKS THE SPOT" is rendered in ciphertext as
Variants
The core elements of this system are the grid and dots. Some systems use the X's, but even these can be rearranged. One commonly used method orders the symbols as shown in the above image: grid, grid, X, X. Another commonly used system orders the symbols as grid, X, grid, X. Another is grid, grid, grid, with each cell having a letter of the alphabet, and the last one having an "&" character. Letters from the first grid have no dot, letters from the second each have one dot, and letters from the third each have two dots. Another variation of this last one is called the Newark Cipher, which instead of dots uses one to three short lines which may be projecting in any length or orientation. This gives the illusion of a larger number of different characters than actually exist.[18]
Another system, used by the Rosicrucians, used a single grid of nine cells, and 1 to 3 dots in each cell or "pen". So ABC would be in the top left pen, followed by DEF and GHI on the first line, then groups of JKL MNO PQR on the second, and STU VWX YZ on the third.[2][14] When enciphered, the location of the dot in each symbol (left, center, or right), would indicate which letter in that pen was represented.[1][14] More difficult systems use a non-standard form of the alphabet, such as writing it backwards in the grid, up and down in the columns,[4] or a completely randomized set of letters.
The Templar cipher is a method claimed to have been used by the Knights Templar. It uses a variant of a Maltese Cross.[19]
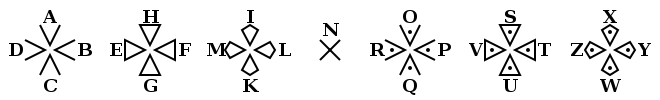
Notes
- Wrixon, pp. 182–183
- Barker, p. 40
- Wrixon, p. 27
- Gardner
- Bauer, Friedrich L. "Encryption Steps: Simple Substitution." Decrypted Secrets: Methods and Maxims of Cryptology (2007): 43.
- Newby, Peter. "Maggie Had A Little Pigpen." Word Ways 24.2 (1991): 13.
- Blavatsky, Helena Petrovna. The Theosophical Glossary. Theosophical Publishing Society, 1892, pg 230
- Mathers, SL MacGregor. The Kabbalah Unveiled. Routledge, 2017, pg 10
- Thompson, Dave. "Elliptic Curve Cryptography." (2016)
- MacNulty, W. K. (2006). Freemasonry: symbols, secrets, significance. London: Thames & Hudson, pg 269
- Parrangan, Dwijayanto G., and Theofilus Parrangan. "New Simple Algorithm for Detecting the Meaning of Pigpen Chiper Boy Scout (“Pramuka”)." International Journal of Signal Processing, Image Processing and Pattern Recognition 6.5 (2013): 305-314.
- Agrippa, Henry Cornelius. "Three Books of Occult Philosophy, or of." JF (London, Gregory Moule, 1650) (1997): 14-15.
- Agrippa, Cornelius. "Three Books of Occult Philosophy", http://www.esotericarchives.com/agrippa/agripp3c.htm#chap30
- Pratt, pp. 142–143
- Hynson, Colin. "Codes and ciphers." 5 to 7 Educator 2006.14 (2006): v-vi.
- Kahn, 1967, p.~772
- Newton, 1998, p. 113
- Glossary of Cryptography
- McKeown, Trevor W. "Purported Templars cipher". freemasonry.bcy.ca. Retrieved 2016-11-07.
References
- Barker, Wayne G., ed. (1978). The History of Codes and Ciphers in the United States Prior to World War I. Aegean Park Press. ISBN 0-89412-026-3.
- Gardner, Martin (1972). Codes, ciphers and secret writing. ISBN 0-486-24761-9.
- Kahn, David (1967). The Codebreakers. The Story of Secret Writing. Macmillan.
- Kahn, David (1996). The Codebreakers. The Story of Secret Writing. Scribner. ISBN 0-684-83130-9.
- Newton, David E. (1998). "Freemason's Cipher". Encyclopedia of Cryptology. ISBN 0-87436-772-7.
- Pratt, Fletcher (1939). Secret and Urgent: The story of codes and ciphers. Aegean Park Press. ISBN 0-89412-261-4.
- Shulman, David; Weintraub, Joseph (1961). A glossary of cryptography. Crypto Press. p. 44.
- Wrixon, Fred B. (1998). Codes, Ciphers, and other Cryptic & Clandestine Communication. Black Dog & Leventhal Publishers, Inc. ISBN 1-57912-040-7.
External links
| Wikimedia Commons has media related to Pigpen cipher. |
- Online Pigpen cipher tool for enciphering small messages.
- Online Pigpen cipher tool for deciphering small messages.
- Cipher Code True Type Font
- Deciphering An Ominous Cryptogram on a Manhattan Tomb presents a Pigpen cipher variant
- Elian script-often considered a variant of Pigpen.