KeRanger
KeRanger (also known as OSX.KeRanger.A) is a ransomware trojan horse targeting computers running macOS. Discovered on March 4, 2016, by Palo Alto Networks, it affected more than 7,000 Mac users.
KeRanger is remotely executed on the victim's computer from a compromised installer for Transmission, a popular BitTorrent client downloaded from the official website. It is hidden in the .dmg file under General.rtf. The .rtf is actually a Mach-O format executable file packed with UPX 3.91. When users click these infected apps, their bundle executable Transmission.app/Content/MacOS/Transmission will copy this General.rtf file to ~/Library/kernel_service and execute this “kernel_service” before any user interface appearing.[1] It encrypts the files with RSA and RSA public key cryptography, with the key for decryption only stored on the attacker's servers. The malware then creates a file, called "readme_to_decrypt.txt", in every folder. When the instructions are opened, it gives the victim directions on how to decrypt the files, usually demanding a payment of one bitcoin. The ransomware is considered to be a variant of the Linux ransomware Linux.Encoder.1.[2]
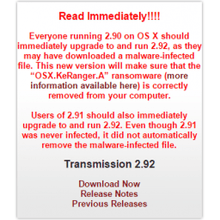
Discovery
On March 4, 2016, Palo Alto Networks added Ransomeware.KeRanger.OSX to their virus database. Two days after, they published a description and a breakdown of the code.
Propagation
According to Palo Alto Research Center, KeRanger was most commonly infected into Transmission from the official website being compromised, then the infected .dmg was uploaded to look like the "real" Transmission. After it was reported, the makers of Transmission issued a new download on the website and pushed out a software update.
The only way the malware infected the victim's computer was by using a valid developer signature issued by Apple, which allowed it to bypass Apple's built-in security.
Encryption process
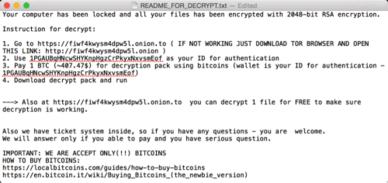
The first time it executes, KeRanger will create three files “.kernel_pid”, “.kernel_time” and “.kernel_complete” under ~/Library directory and write the current time to “.kernel_time”. It will then sleep for three days.[1] After that, it will collect information about the Mac, which includes the model name and the UUID. After it collects the information, it uploads it to one of its Command and Control servers. These servers’ domains are all sub-domains of onion[.]link or onion[.]nu, two domains that host servers only accessible over the Tor network. After it connects with the Command and Control servers, it returns the data with a "README_FOR_DECRYPT.txt" file. It then tells the user that their files have been encrypted, etc. and that they need to pay a sum of one bitcoin, which is roughly $400 in United States dollar.
KeRanger encrypts each file (e.g. Test.docx) by first creating an encrypted version that uses the .encrypted extension (i.e. Test.docx.encrypted.) To encrypt each file, KeRanger starts by generating a random number (RN) and encrypts the RN with the RSA key retrieved from the C2 server using the RSA algorithm. It then stores the encrypted RN at the beginning of resulting file. Next, it will generate an Initialization Vector (IV) using the original file’s contents and store the IV inside the resulting file. After that, it will mix the RN and the IV to generate an AES encryption key. Finally, it will use this AES key to encrypt the contents of the original file and write all encrypted data to the result file.
Encrypted files
After connecting to the C2 server, it will retrieve the encryption key, then start the process. It will first encrypt the "/Users" folder, then after that "/Volumes" There are also 300 file extensions that are encrypted, such as:
- Documents: .doc, .docx, .docm, .dot, .dotm, .ppt, .pptx, .pptm, .pot, .potx, .potm, .pps, .ppsm, .ppsx, .xls, .xlsx, .xlsm, .xlt, .xltm, .xltx, .txt, .csv, .rtf, .te
- Images: .jpg, .jpeg
- Audio and video: .mp3, .mp4, .avi, .mpg, .wav, .flac
- Archives: .zip, .rar., .tar, .gzip
- Source code: .cpp, .asp, .csh, .class, .java, .lua
- Database: .db, .sql
- Email: .eml
- Certificate: .pem
References
- Xiao, Claud; Chen, Jin. "New OS X Ransomware KeRanger Infected Transmission BitTorrent Client Installer - Palo Alto Networks Blog". Palo Alto Networks Blog. Retrieved 2016-03-10.
- "KeRanger Is Actually A Rewrite of Linux.Encoder". Bitdefender Labs. Retrieved 28 March 2016.