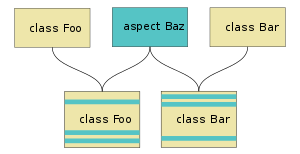
Cross-cutting concern
In aspect-oriented software development, cross-cutting concerns are aspects of a program that affect other concerns. These concerns often cannot be cleanly decomposed from the rest of the system in both the design and implementation, and can result in either scattering (code duplication), tangling (significant dependencies between systems), or both.
For instance, if writing an application for handling medical records, the indexing of such records is a core concern, while logging a history of changes to the record database or user database, or an authentication system, would be cross-cutting concerns since they interact with more parts of the program.
Background
Cross-cutting concerns are parts of a program that rely on or must affect many other parts of the system. They form the basis for the development of aspects.[1] Such cross-cutting concerns do not fit cleanly into object-oriented programming or procedural programming.[2]
Cross-cutting concerns can be directly responsible for tangling, or system inter-dependencies, within a program. Because procedural and functional language constructs consist entirely of procedure calling, there is no semantic through which two goals (the capability to be implemented and the related cross-cutting concern) can be addressed simultaneously.[3] As a result, the code addressing the cross-cutting concern must be scattered, or duplicated, across the various related locations, resulting in a loss of modularity.[2]
Aspect-oriented programming aims to encapsulate cross-cutting concerns into aspects to retain modularity. This allows for the clean isolation and reuse of code addressing the cross-cutting concern.[4] By basing designs on cross-cutting concerns, software engineering benefits can include modularity and simplified maintenance.[5]
Examples
Examples of concerns that tend to be cross-cutting include:
- Business rules
- Caching
- Code mobility
- Data validation
- Domain-specific optimizations
- Error detection and correction
- Internationalization and localization which includes Language localisation
- Information security
- Logging
- Memory management
- Monitoring
- Persistence
- Product features
- Real-time constraints
- Synchronization
- Transaction processing
- Context-sensitive help
See also
- Separation of concerns
- Aspect-oriented programming
- Code refactoring (restructuring software)
- Database normalization (minimize needlessly replicated data)
- Multiple inheritance
- Microservices
- Orthogonalization (mathematical normalization)
References
- Kiczales et. al 2002, p. 4
- Kiczales et al. 1997, p. 1
- Kiczales et al. 1997, p. 6
- Kiczales et al. 1997, p. 2
- Li, Krishnamurthi & Fisler 2002, p. 1
Bibliography
- Kiczales, Gregor; Lamping, John; Mendhekar, Anurag; Maeda, John; Lopes, Cristina; Longtier, Jean-Marc; Irwin (1997). "Aspect-Oriented Programming". Proceedings of the 11th European Conference on Object-Oriented Programming (ECOOP 1997): 220–242.CS1 maint: ref=harv (link)
- US patent 6467086, Kiczales et. al, "Aspect-oriented programming", issued 2002-10-15
- Li, Harry; Krishnamurthi, Shriram; Fisler, Kathi (2002). "Verifying Cross-Cutting Features as Open Systems". ACM SIGSOFT Software Engineering Notes. 27 (6): 89–98. CiteSeerX 10.1.1.8.9445. doi:10.1145/605466.605481.CS1 maint: ref=harv (link)
- Parnas, David L. (December 1972). "On the Criteria To Be Used in Decomposing Systems into Modules". Communications of the ACM. 15 (12): 1053–1058. CiteSeerX 10.1.1.90.8963. doi:10.1145/361598.361623.
- Tarr, Peri; Ossher, Harold; Harrison, William; Sutton, Stanley M., Jr. (1999). N Degrees of Separation: Multi- Dimensional Separation of Concerns. Proceedings of the 21st International Conference on Software Engineering. Los Angeles, California, USA: IEEE Computer Society Press. pp. 107–119. CiteSeerX 10.1.1.89.1641. doi:10.1109/ICSE.1999.841000. ISBN 978-1581130744.
Further reading
- Laddad, R. (2003): AspectJ in Action, Practical Aspect-Oriented Programming, Manning Publications Co.
External links
- AOSD.net's glossary of aspect oriented terms (via Internet Archive Wayback Machine; AOSD.net has become Modularity).
- AspectJ , an Aspect-Oriented extension to the Java programming language
- Bergmans, L., M. Aksit (2001): Composing Multiple Concerns Using Composition Filters, https://web.archive.org/web/20170909131212/http://trese.cs.utwente.nl/ (24 July 2004)
- Berg, K. van den, Conejero, J. and Chitchyan, R. (2005). AOSD Ontology 1.0 ‐ Public Ontology of Aspect‐Orientation. AOSD Europe Network of Excellence, http://eprints.eemcs.utwente.nl/10220/01/BergConChi2005.pdf
- Here is an example of handling a cross-cutting concern: https://web.archive.org/web/20161220151503/https://www.captechconsulting.com/blogs/a-persistence-pattern-using-threadlocal-and-ejb-interceptors