1
I am using Putty to achieve SSH Reverse Tunnel Port Forwarding. Most of the tutorials are teaching me to forward remote port to localhost port. However, may I know is it make sense to input other host such as 192.168.1.132:8081 into the Destination field?
I have tried to do that. 192.168.1.132:8081 is a working web server with a contented page, but I got ERR_EMPTY_RESPONSE when I visit localhost:12345 (I set port 12345 as the source port) from the client device.
My Putty Configurations
Outgoing Proxy configuration:
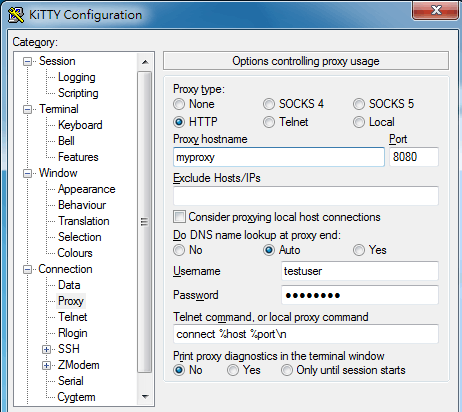
Tunneling config (the Dynamic one is for the Socks5 connection, please just ignore it; the R12345 one is the tunnel that I am playing with):
The result that I try to access the tunnel from the Destination (SSH Server):
Can anyone help me?
UPDATE 1
In the device that I am running SSH command, I am going out with via a proxy server. Is that affecting the reverse tunnel behavior?
UPDATE 2
I have tried to make the reverse tunnel from the http server directly. However, in the SSH server I can visit the website by http://localhost:12345. Attched setting and result at below.
Same, http server needed to go out via my office's http proxy too!
Create a reverse tunnel from http server
And then I can visit the http server from SSH server via localhost:12345

@KamilMaciorowski Sorry for undetailed question. I have updated the question with some image. – mannok – 2018-01-19T07:08:42.800
1What happens when you browse
192.168.1.132:8081from the SSH client? (with no SSH involved in this case at all). Do you see proper page? – Kamil Maciorowski – 2018-01-19T07:21:11.310@KamilMaciorowski Sure, normal page, normal performance – mannok – 2018-01-19T07:34:43.263
1
Please read this. The HTTP server at
– Kamil Maciorowski – 2018-01-19T07:44:34.357192.168.1.132:8081may ignore requests destined to addresses other than192.168.1.132. When you connect from the remote side of your SSH connection, the address islocalhost:12345and it doesn't fit. If the tunnel didn't work at all, you would getERR_CONNECTION_REFUSED, notERR_EMPTY_RESPONSE. TOOGAM's answer is right: in general you can build tunnels this way.@KamilMaciorowski I see. That means the empty response is generated by the http server right? Because of invalid domain/hostname? But when I type localhost:8081 is the http server, I can access the page. In this case the requesting hosename is localhost too! – mannok – 2018-01-19T08:01:32.320
"That means the empty response is generated by the http server right?" – I think so. When you type
localhost:8081on the HTTP server, the request goes through its loopback interface. Requests from other computers arrive from elsewhere (like viaeth0or so). I guess this does matter when the HTTP server software checks sanity of these requests. – Kamil Maciorowski – 2018-01-19T08:12:18.290@KamilMaciorowski Thank you very much for your patient reply!!! But I have try another test just now and updated in update 2. I make the tunnel directly from http server this time and it works and I can visit the http server from SSH server!! This makes me so confuse... – mannok – 2018-01-19T08:26:33.417
You're abusing the concept of the site. You had one question, it was answered by TOOGAM. My comments were only to convince you your results are not against this answer you got (the issue is not with SSH). Comments are not for solving additional questions, really. But OK, let's try. The local side of your connection passes packets to
localhost:8081, so to the loopback interface. The HTTP server seeslocalhost:12345used in the address of the request incoming from the loopback interface. The server probably doesn't mind another port, the rest fits. These are nuances of the server, not SSH. – Kamil Maciorowski – 2018-01-19T08:40:08.850To avoid possible peculiarities of HTTP servers you may play with listening
netcatbeing the target of your tunnel. – Kamil Maciorowski – 2018-01-19T08:43:28.757To easily test if the web server is only responding if it's accessed as http://192.168.1.132:8081, you can try what http://192.168.1.132.xip.io:8081 gives you. (See http://xip.io for documentation.)
– Arjan – 2018-01-19T11:03:10.963Check the access log/errorlog on the destination http server and the browser network console of the tries with and without ssh tunnel to verify no http redirects are executed. (And yes, this is a Problem outside of the ssh setup i.e. not your original question anymore). – eckes – 2018-12-07T00:31:54.213