How does windows file sharing actually work?
The security model used in Microsoft SMB Protocol is identical to the
one used by other variants of SMB, and consists of two levels of
security—user and share. A share is a file, directory, or printer that
can be accessed by Microsoft SMB Protocol clients.
User-level authentication indicates that the client attempting to
access a share on a server must provide a user name and password. When
authenticated, the user can then access all shares on a server not
also protected by share-level security. This security level allows
system administrators to specifically determine which users and groups
can access a share.
Share-level authentication indicates that access to a share is
controlled by a password assigned to that share only. Unlike
user-level security, this security level does not require a user name
for authentication and no user identity is established.
Under both of these security levels, the password is encrypted before
it is sent to the server. NTLM and the older LAN Manager (LM)
encryption are supported by Microsoft SMB Protocol. Both encryption
methods use challenge-response authentication, where the server sends
the client a random string and the client returns a computed response
string that proves the client has sufficient credentials for access.
source
The Server Message Block (SMB) Protocol is a network file sharing
protocol, and as implemented in Microsoft Windows is known as
Microsoft SMB Protocol. The set of message packets that defines a
particular version of the protocol is called a dialect. The Common
Internet File System (CIFS) Protocol is a dialect of SMB. Both SMB and
CIFS are also available on VMS, several versions of Unix, and other
operating systems.
The technical reference to CIFS is available from Microsoft
Corporation at Common Internet File System (CIFS) File Access
Protocol.
Although its main purpose is file sharing, additional Microsoft SMB
Protocol functionality includes the following:
In the OSI networking model, Microsoft SMB Protocol is most often used
as an Application layer or a Presentation layer protocol, and it
relies on lower-level protocols for transport. The transport layer
protocol that Microsoft SMB Protocol is most often used with is
NetBIOS over TCP/IP
(NBT).
However, Microsoft SMB Protocol can also be used without a separate
transport protocol—the Microsoft SMB Protocol/NBT combination is
generally used for backward compatibility.
The Microsoft SMB Protocol is a client-server implementation and
consists of a set of data packets, each containing a request sent by
the client or a response sent by the server. These packets can be
broadly classified as follows:
- Session control packets—Establishes and discontinues a connection to shared server resources.
- File access packets—Accesses and manipulates files and directories on the remote server.
- General message packets—Sends data to print queues, mailslots, and named pipes, and provides data about the status of print queues.
Some message packets may be grouped and sent in one transmission to
reduce response latency and increase network bandwidth. This is called
"batching." The Microsoft SMB Protocol Packet Exchange
Scenario
section describes an example of a Microsoft SMB Protocol session that
uses packet batching.
Topic: Microsoft SMB Protocol Dialects
- Description: To establish a connection between a client and a server using Microsoft SMB Protocol, you must first determine the
dialect with the highest level of functionality that both the client
and server support.
Topic: Microsoft SMB Protocol Authentication
- Description: The security model used in Microsoft SMB Protocol is identical to the one used by other variants of SMB, and consists of
two levels of security—user and share. A share is a file, directory,
or printer that can be accessed by Microsoft SMB Protocol clients.
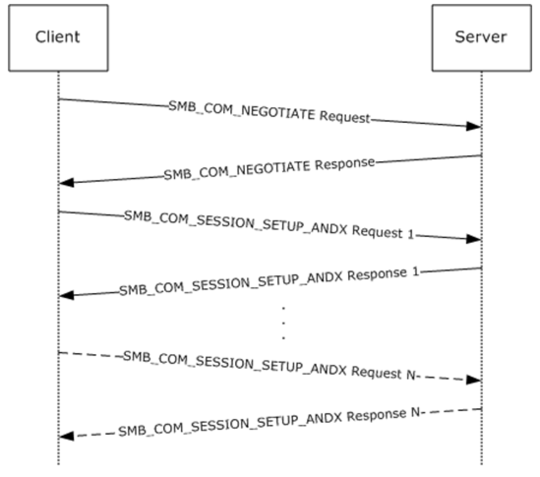
Topic: Microsoft SMB Protocol Packet Exchange Scenario
- Description: Example of a Microsoft SMB Protocol packet exchange between a client and a server.
source
Comment Clarification
File access packets—Accesses and manipulates files and directories on the remote server.' How does this happen? Where is the response packet to give the requested data to client? Kraken
Each packet is typically a basic request of some kind, such as open
file, close file, or read file. The server then receives the packet,
checks to see if the request is legal, verifies the client has the
appropriate file permissions, and finally executes the request and
returns a response packet to the client. The client then parses the
response packet and can determine whether or not the initial request
was successful.
source
Further Resources
A diagram and an explanation of the authentication aspects involved in establishing a client-server session with the protocol.
Reads for further detail on SMB.
1I just added a quoted answers from Microsoft resources for how Windows file sharing works protocol and authentication wise. This should tell you what you need for all your questions. – Pimp Juice IT – 2016-09-03T21:35:21.210