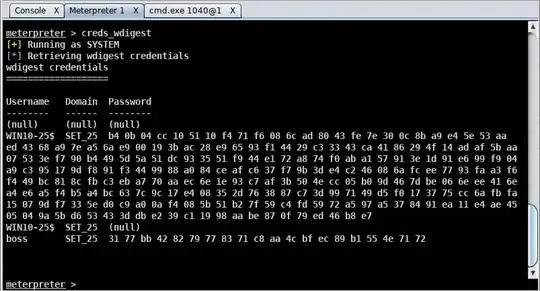
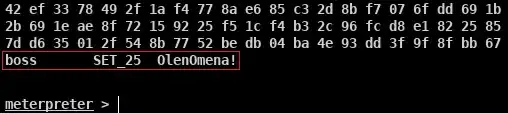
No to avoid it, as to steal kerberos ticket or NTLM hash keep in mind the user must be a local administrator, and the application must be run as a admin too.
Please see that note from mimikatz;
Run Mimikatz as Administrator: Mimikatz needs to be “Run as Admin” to function completely, even if you are using an Administrator account.
As such it fall into the 10 immutable laws of security; See the one in bold;
Law #1: If a bad guy can persuade you to run his program on your
computer, it's not solely your computer anymore.
Law #2: If a bad guy can alter the operating system on your computer, it's not your computer anymore.
Law #3: If a bad guy has unrestricted physical
access to your computer, it's not your computer anymore.
Law #4: If
you allow a bad guy to run active content in your website, it's not
your website any more.
Law #5: Weak passwords trump strong security.
Law #6: A computer is only as secure as the administrator is trustworthy.
Law #7: Encrypted data is only as secure as its
decryption key.
Law #8: An out-of-date antimalware scanner is only
marginally better than no scanner at all.
Law #9: Absolute anonymity
isn't practically achievable, online or offline.
Law #10: Technology
is not a panacea.
As you fall into the 10 immutable laws of security, Microsoft will never fix that, as a admin can do anything on the computer, even installing a keylogger, who know, as you must understand it's more how you protect your environment against such attack vector that is important.
So at first I would suggest to use restricted group GPO to make sure no one can add itselft to the local admin group.
Secondly I would remove all other boot device than the HDD to secure who can boot on a flash device, to prevent someone that could wipe a local admin account's password.
Thirdly I would protect with a strong password the BIOS.
Lastly, I would use a encryption method for the hard disk, to prevent non-authorized change by a cold boot if someone remove the hard disk from the machine.
There is surelly other tips, but you must abide to a strong security's model if you want to secure your enterprise work space, and enable account auditing if you want to catch a bad actor.