Configuration
- A Windows 2008R2 RDS server
RDS01 - A Windows 2008R2 RDS server
RDS02 - A Windows 2012R2 RemoteApp server
APP01
Problem
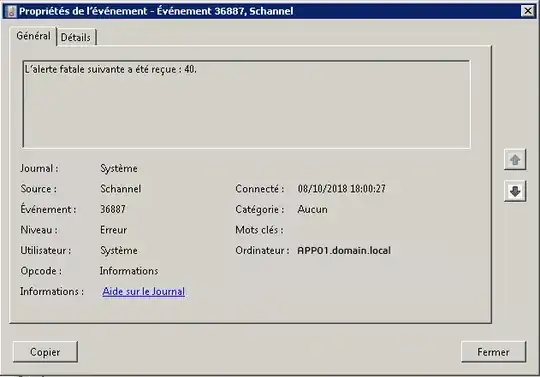
Calling URL https://APP01.domain.local/rdweb :
- From
RDS01: Schannel error 40 (handshake_failure)
- From
RDS02: Response code 200, cert chain OK
Diagnose
Using ssldiagnos.exe from RDS01 (handshake failure removed):
-= SUMMARY =-
Weak: 0
Intermediate: 0
Strong: 0
APP01 accepts 0 SSL handshake configurations
Using ssldiagnos.exe from RDS02 (handshake failure removed):
[+] Testing STRONG: TLS 1, ECDHE-RSA-AES256-SHA (256 bits) ... CONNECT_OK SEND_OK RECEIVE_OK CERT_OK
[+] Testing STRONG: TLS 1, DHE-RSA-AES256-SHA (256 bits) ... CONNECT_OK SEND_OK RECEIVE_OK CERT_OK
[+] Testing STRONG: TLS 1, ECDHE-RSA-AES128-SHA (128 bits) ... CONNECT_OK SEND_OK RECEIVE_OK CERT_OK
[+] Testing STRONG: TLS 1, DHE-RSA-AES128-SHA (128 bits) ... CONNECT_OK SEND_OK RECEIVE_OK CERT_OK
[+] Testing STRONG: TLS 1.1, ECDHE-RSA-AES256-SHA (256 bits) ... CONNECT_OK SEND_OK RECEIVE_OK CERT_OK
[+] Testing STRONG: TLS 1.1, DHE-RSA-AES256-SHA (256 bits) ... CONNECT_OK SEND_OK RECEIVE_OK CERT_OK
[+] Testing STRONG: TLS 1.1, ECDHE-RSA-AES128-SHA (128 bits) ... CONNECT_OK SEND_OK RECEIVE_OK CERT_OK
[+] Testing STRONG: TLS 1.2, ECDHE-RSA-AES256-SHA384 (256 bits) ... CONNECT_OK SEND_OK RECEIVE_OK CERT_OK
[+] Testing STRONG: TLS 1.2, ECDHE-RSA-AES256-SHA (256 bits) ... CONNECT_OK SEND_OK RECEIVE_OK CERT_OK
[+] Testing STRONG: TLS 1.2, DHE-RSA-AES256-GCM-SHA384 (256 bits) ... CONNECT_OK SEND_OK RECEIVE_OK CERT_OK
[+] Testing STRONG: TLS 1.2, DHE-RSA-AES256-SHA (256 bits) ... CONNECT_OK SEND_OK RECEIVE_OK CERT_OK
[+] Testing STRONG: TLS 1.2, ECDHE-RSA-AES128-SHA256 (128 bits) ... CONNECT_OK SEND_OK RECEIVE_OK CERT_OK
[+] Testing STRONG: TLS 1.2, ECDHE-RSA-AES128-SHA (128 bits) ... CONNECT_OK SEND_OK RECEIVE_OK CERT_OK
[+] Testing STRONG: TLS 1.2, DHE-RSA-AES128-GCM-SHA256 (128 bits) ... CONNECT_OK SEND_OK RECEIVE_OK CERT_OK
[+] Testing STRONG: TLS 1.2, DHE-RSA-AES128-SHA (128 bits) ... CONNECT_OK SEND_OK RECEIVE_OK CERT_OK
-= SUMMARY =-
Weak: 0
Intermediate: 0
Strong: 15
APP01 accepts 15 SSL handshake configurations
Schannel
Help
Any help to solve this issue will be welcome
Edit 1
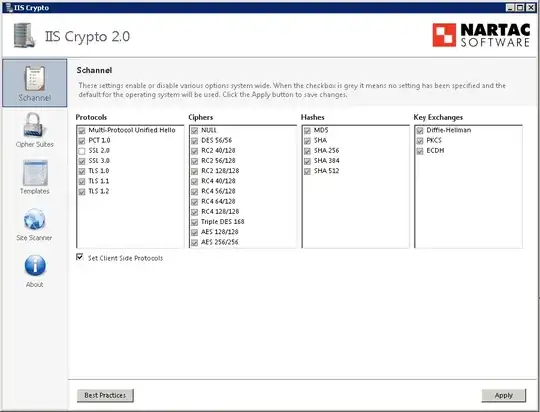
Here, the RDS01 SCHANNEL registry hive export after enabling all (except SSL 2.0) manually with IIS Crypto to explicitly declare them as enabled
{schannel}=HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL
[{schannel}]
"EventLogging"=dword:00000001
[{schannel}\Ciphers]
[{schannel}\Ciphers\AES 128/128]
"Enabled"=dword:ffffffff
[{schannel}\Ciphers\AES 256/256]
"Enabled"=dword:ffffffff
[{schannel}\Ciphers\DES 56/56]
"Enabled"=dword:ffffffff
[{schannel}\Ciphers\NULL]
"Enabled"=dword:ffffffff
[{schannel}\Ciphers\RC2 128/128]
"Enabled"=dword:ffffffff
[{schannel}\Ciphers\RC2 40/128]
"Enabled"=dword:ffffffff
[{schannel}\Ciphers\RC2 56/128]
"Enabled"=dword:ffffffff
[{schannel}\Ciphers\RC4 128/128]
"Enabled"=dword:ffffffff
[{schannel}\Ciphers\RC4 40/128]
"Enabled"=dword:ffffffff
[{schannel}\Ciphers\RC4 56/128]
"Enabled"=dword:ffffffff
[{schannel}\Ciphers\RC4 64/128]
"Enabled"=dword:ffffffff
[{schannel}\Ciphers\Triple DES 168]
"Enabled"=dword:ffffffff
[{schannel}\CipherSuites]
[{schannel}\Hashes]
[{schannel}\Hashes\MD5]
"Enabled"=dword:ffffffff
[{schannel}\Hashes\SHA]
"Enabled"=dword:ffffffff
[{schannel}\Hashes\SHA256]
"Enabled"=dword:ffffffff
[{schannel}\Hashes\SHA384]
"Enabled"=dword:ffffffff
[{schannel}\Hashes\SHA512]
"Enabled"=dword:ffffffff
[{schannel}\KeyExchangeAlgorithms]
[{schannel}\KeyExchangeAlgorithms\Diffie-Hellman]
"Enabled"=dword:ffffffff
[{schannel}\KeyExchangeAlgorithms\ECDH]
"Enabled"=dword:ffffffff
[{schannel}\KeyExchangeAlgorithms\PKCS]
"Enabled"=dword:ffffffff
[{schannel}\Protocols]
[{schannel}\Protocols\Multi-Protocol Unified Hello]
[{schannel}\Protocols\Multi-Protocol Unified Hello\Client]
"Enabled"=dword:ffffffff
"DisabledByDefault"=dword:00000000
[{schannel}\Protocols\Multi-Protocol Unified Hello\Server]
"Enabled"=dword:ffffffff
"DisabledByDefault"=dword:00000000
[{schannel}\Protocols\PCT 1.0]
[{schannel}\Protocols\PCT 1.0\Client]
"Enabled"=dword:ffffffff
"DisabledByDefault"=dword:00000000
[{schannel}\Protocols\PCT 1.0\Server]
"Enabled"=dword:ffffffff
"DisabledByDefault"=dword:00000000
[{schannel}\Protocols\SSL 2.0]
[{schannel}\Protocols\SSL 2.0\Client]
"DisabledByDefault"=dword:00000001
"Enabled"=dword:00000000
[{schannel}\Protocols\SSL 2.0\Server]
"Enabled"=dword:00000000
"DisabledByDefault"=dword:00000001
[{schannel}\Protocols\SSL 3.0]
[{schannel}\Protocols\SSL 3.0\Client]
"Enabled"=dword:ffffffff
"DisabledByDefault"=dword:00000000
[{schannel}\Protocols\SSL 3.0\Server]
"Enabled"=dword:ffffffff
"DisabledByDefault"=dword:00000000
[{schannel}\Protocols\TLS 1.0]
[{schannel}\Protocols\TLS 1.0\Client]
"Enabled"=dword:ffffffff
"DisabledByDefault"=dword:00000000
[{schannel}\Protocols\TLS 1.0\Server]
"Enabled"=dword:ffffffff
"DisabledByDefault"=dword:00000000
[{schannel}\Protocols\TLS 1.1]
[{schannel}\Protocols\TLS 1.1\Client]
"Enabled"=dword:ffffffff
"DisabledByDefault"=dword:00000000
[{schannel}\Protocols\TLS 1.1\Server]
"Enabled"=dword:ffffffff
"DisabledByDefault"=dword:00000000
[{schannel}\Protocols\TLS 1.2]
[{schannel}\Protocols\TLS 1.2\Client]
"Enabled"=dword:ffffffff
"DisabledByDefault"=dword:00000000
[{schannel}\Protocols\TLS 1.2\Server]
"Enabled"=dword:ffffffff
"DisabledByDefault"=dword:00000000