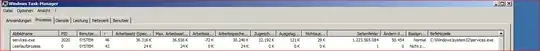
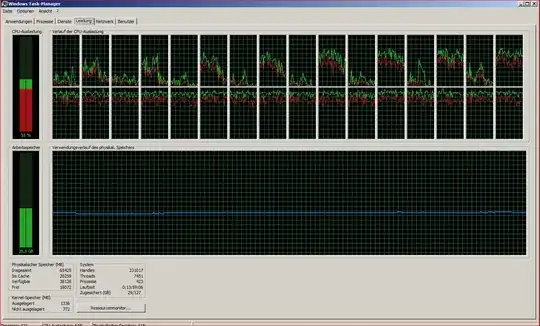
After last windows updates, we have high cpu load and page faults on services.exe aprox 2% cpu per Session... we deinstalled all windows updates done on this date , but situation is persistant. processexplorer reveals for services.exe only ntdll as consumer ...
How to debug and resolve this issue ?