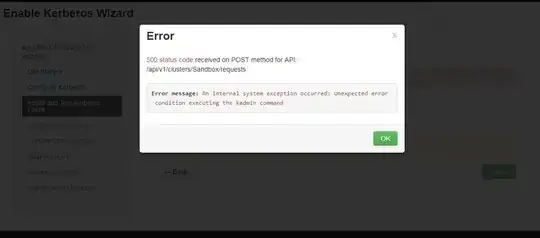
We want to integrate our existing security setup (Apache Knox, OpenLDAP, Apache Ranger) with Kerberos. So what I understood through some blogs that we can use OpenLDAP as a back-end for the Kerberos database.
But facing some issues and confusion over the below points:
While integrating LDAP with Kerberos, I am not able to create a container with
ou. It seem to be only working withcn?After changing to
cnI can see Kerberos is talking to OpenLDAP and has created container and principals, but when connecting through Apache Ambari, I am getting the attached error. Both KDC and Sandbox are on different servers.
The hostname for KDC server is kdcserver. Note: I am able to telnet the KDC server over the port 749.
Attaching error message, krb5.conf and LDAP ldiff file:
KRB5 conf
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
default_realm = ABC.COM
dns_lookup_realm = false
dns_lookup_kdc = false
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = true
allow_weak_crypto = true
default_tkt_enctypes = des-cbc-md5 des-cbc-crc des3-cbc-sha1
default_tgs_enctypes = des-cbc-md5 des-cbc-crc des3-cbc-sha1
[realms]
ABC.COM = {
kdc = kdcserver
admin_server = kdcserver
default_domain= kdcserver
database_module = openldap_ldapconf
}
[appdefaults]
pam = {
debug = false
ticket_lifetime = 36000
renew_lifetime = 36000
forwardable = true
krb4_convert = false
}
[dbmodules]
openldap_ldapconf = {
db_library = kldap
ldap_kerberos_container_dn = cn=kerberos,dc=abc,dc=com
ldap_kdc_dn = "cn=manager,dc=abc,dc=com"
ldap_kadmind_dn = "cn=manager,dc=abc,dc=com"
ldap_service_password_file = /etc/krb5.d/stash.keyfile
ldap_servers = ldap://kdcserver
ldap_conns_per_server = 5
}
LDAP ldiff
dn: dc=abc,dc=com
objectClass: top
objectClass: dcObject
objectClass: organization
o: abchadoop
dc: ABC
dn: ou=groups,dc=abc,dc=com
objectClass: top
objectClass: organizationalUnit
ou: groups
description: LDAP Group
dn: ou=services,dc=abc,dc=com
objectClass: top
objectClass: organizationalUnit
ou: services
dn: cn=hcat,ou=services,dc=abc,dc=com
objectClass: top
objectClass: applicationProcess
objectClass: simpleSecurityObject
cn: hcat
userPassword: hcat-password
dn: cn=hdfs,ou=services,dc=abc,dc=com
objectClass: top
objectClass: applicationProcess
objectClass: simpleSecurityObject
cn: hdfs
userPassword: hdfs-password
dn: cn=yarn,ou=services,dc=abc,dc=com
objectClass: top
objectClass: applicationProcess
objectClass: simpleSecurityObject
cn: yarn
userPassword: yarn-password
dn: cn=mapred,ou=services,dc=abc,dc=com
objectClass: top
objectClass: applicationProcess
objectClass: simpleSecurityObject
cn: mapred
userPassword: mapred-password
dn: cn=hbase,ou=services,dc=abc,dc=com
objectClass: top
objectClass: applicationProcess
objectClass: simpleSecurityObject
cn: hbase
userPassword: hbase-password
dn: cn=zookeeper,ou=services,dc=abc,dc=com
objectClass: top
objectClass: applicationProcess
objectClass: simpleSecurityObject
cn: zookeeper
userPassword: zookeeper-password
dn: cn=oozie,ou=services,dc=abc,dc=com
objectClass: top
objectClass: applicationProcess
objectClass: simpleSecurityObject
cn: oozie
userPassword: oozie-password
dn: cn=hive,ou=services,dc=abc,dc=com
objectClass: top
objectClass: applicationProcess
objectClass: simpleSecurityObject
cn: hive
userPassword: hive-password
dn: cn=hcat,ou=groups,dc=abc,dc=com
objectClass: top
objectClass: groupOfNames
cn: hcat
member: cn=hcat,ou=services,dc=abc,dc=com
dn: cn=hdfs,ou=groups,dc=abc,dc=com
objectClass: top
objectClass: groupOfNames
cn: hdfs
member: cn=hdfs,ou=services,dc=abc,dc=com
dn: cn=yarn,ou=groups,dc=abc,dc=com
objectClass: top
objectClass: groupOfNames
cn: yarn
member: cn=yarn,ou=services,dc=abc,dc=com
dn: cn=mapred,ou=groups,dc=abc,dc=com
objectClass: top
objectClass: groupOfNames
cn: mapred
member: cn=mapred,ou=services,dc=abc,dc=com
dn: cn=hbase,ou=groups,dc=abc,dc=com
objectClass: top
objectClass: groupOfNames
cn: hbase
member: cn=hbase,ou=services,dc=abc,dc=com
dn: cn=zookeeper,ou=groups,dc=abc,dc=com
objectClass: top
objectClass: groupOfNames
cn: zookeeper
member: cn=zookeeper,ou=services,dc=abc,dc=com
dn: cn=oozie,ou=groups,dc=abc,dc=com
objectClass: top
objectClass: groupOfNames
cn: oozie
member: cn=oozie,ou=services,dc=abc,dc=com
dn: cn=hive,ou=groups,dc=abc,dc=com
objectClass: top
objectClass: groupOfNames
cn: hive
member: cn=hive,ou=services,dc=abc,dc=com
dn: cn=hadoop,ou=groups,dc=abc,dc=com
objectClass: top
objectClass: groupOfNames
cn: hadoop
member: cn=hcat,ou=services,dc=abc,dc=com
member: cn=hdfs,ou=services,dc=abc,dc=com
member: cn=yarn,ou=services,dc=abc,dc=com
member: cn=mapred,ou=services,dc=abc,dc=com
member: cn=hbase,ou=services,dc=abc,dc=com
member: cn=zookeeper,ou=services,dc=abc,dc=com
member: cn=oozie,ou=services,dc=abc,dc=com
member: cn=hive,ou=services,dc=abc,dc=com
dn: ou=temp,dc=abc,dc=com
objectClass: top
objectClass: organizationalUnit
ou: temp
dn: cn=kerberos,dc=abc,dc=com
objectClass: krbContainer
cn: kerberos
dn: cn=ABC.COM,cn=kerberos,dc=abc,dc=com
cn: ABC.COM
objectClass: top
objectClass: krbRealmContainer
objectClass: krbTicketPolicyAux
krbSubTrees: dc=abc,dc=com
dn: krbPrincipalName=K/M@ABC.COM,cn=ABC.COM,cn=kerberos,dc=abc,dc=com
krbLoginFailedCount: 0
krbMaxTicketLife: 86400
krbMaxRenewableAge: 0
krbTicketFlags: 64
krbPrincipalName: K/M@ABC.COM
krbPrincipalExpiration: 19700101000000Z
krbPrincipalKey:: MG6gAwIBAaEDAgEBogMCAQGjAwIBAKRYMFYwVKAHMAWgAwIBAKFJMEegAwIBEq
FABD4gACudDckNzjqfNLNduN5RERcEp/phS6+G/h0Wdup2/y+Y9bNOP0PMQdE3Fu6UJRKixPiMUPH59
mprnoPpkQ==
krbLastPwdChange: 19700101000000Z
krbExtraData:: AAkBAAEALWmiWg==
krbExtraData:: AAItaaJaZGJfY3JlYXRpb25AU1RDSERQLkNPTQA=
krbExtraData:: AAcBAAIAAhMIAQAAAAA=
objectClass: krbPrincipal
objectClass: krbPrincipalAux
objectClass: krbTicketPolicyAux
dn: krbPrincipalName=krbtgt/ABC.COM@ABC.COM,cn=ABC.COM,cn=kerberos,dc=abc,dc=com
krbLoginFailedCount: 0
krbMaxTicketLife: 86400
krbMaxRenewableAge: 0
krbTicketFlags: 0
krbPrincipalName: krbtgt/ABC.COM@ABC.COM
krbPrincipalExpiration: 19700101000000Z
krbPrincipalKey:: MIIBTKADAgEBoQMCAQGiAwIBAaMDAgEApIIBNDCCATAwVKAHMAWgAwIBAKFJME
egAwIBEqFABD4gAHaAH+zsuGSt6J3isOKXez4Nu2LRShW6wreSizhdEyqxBO+3aJDXgLWi4WvWzc86F
7wKyab1qt4ZwiQ16jBEoAcwBaADAgEAoTkwN6ADAgERoTAELhAAwYBS8GIaaJH4PQYo8FFMsA/GSNmv
cjweFhdJq6NYs0mmJDJHiBIeKifNPP0wTKAHMAWgAwIBAKFBMD+gAwIBEKE4BDYYAIfx7NqeVW0Qdj3
VY3r7A/EWzE39RTeU4YfVvOiLLF7llwnmhVBOwxS6//+8VhfbLthC/CMwRKAHMAWgAwIBAKE5MDegAw
IBF6EwBC4QAD/64qF/jbLScov2PillRnkUwTZZC9cWqs8g2YQMNlldaGMAo5pJyGTjxAWB
krbLastPwdChange: 19700101000000Z
krbExtraData:: AAItaaJaZGJfY3JlYXRpb25AU1RDSERQLkNPTQA=
krbExtraData:: AAcBAAIAAhMIAQAAAAA=
objectClass: krbPrincipal
objectClass: krbPrincipalAux
objectClass: krbTicketPolicyAux
dn: krbPrincipalName=kadmin/admin@ABC.COM,cn=ABC.COM,cn=kerberos,dc=abc,dc=com
krbLoginFailedCount: 0
krbMaxTicketLife: 10800
krbMaxRenewableAge: 0
krbTicketFlags: 4
krbPrincipalName: kadmin/admin@ABC.COM
krbPrincipalExpiration: 19700101000000Z
krbPrincipalKey:: MIIBTKADAgEBoQMCAQGiAwIBAaMDAgEApIIBNDCCATAwVKAHMAWgAwIBAKFJME
egAwIBEqFABD4gAC2wcqF48ii/FgncQ0tCL1RoeKaJvzKduUG53bVCAVnQZgaKmD/7yU90fWLqXvw04
0eaoGoOd3h7OUNVkjBEoAcwBaADAgEAoTkwN6ADAgERoTAELhAAaGRk0ddcEM5kHP48daKTkwOMSpA9
OcEA5eIC8MkrTWvBCdfv051k1VlZmzcwTKAHMAWgAwIBAKFBMD+gAwIBEKE4BDYYAHfX7kKE1WMVjT6
XO2fiGH2gKmHP2HIPohKSksmS/hkBlLT137bt4CEbkBftJO5UDBTts0IwRKAHMAWgAwIBAKE5MDegAw
IBF6EwBC4QAPLSVWzkyPn9jsqVmqVjtNWE78Q7VlYKfzMmOLfbi75QwfUn4LdUiM5bt0dF
krbLastPwdChange: 19700101000000Z
krbExtraData:: AAItaaJaZGJfY3JlYXRpb25AU1RDSERQLkNPTQA=
krbExtraData:: AAcBAAIAAnQuQ09NAAA=
objectClass: krbPrincipal
objectClass: krbPrincipalAux
objectClass: krbTicketPolicyAux
dn: krbPrincipalName=kadmin/changepw@ABC.COM,cn=ABC.COM,cn=kerberos,dc=abc,dc=com
krbLoginFailedCount: 0
krbMaxTicketLife: 300
krbMaxRenewableAge: 0
krbTicketFlags: 8196
krbPrincipalName: kadmin/changepw@ABC.COM
krbPrincipalExpiration: 19700101000000Z
krbPrincipalKey:: MIIBTKADAgEBoQMCAQGiAwIBAaMDAgEApIIBNDCCATAwVKAHMAWgAwIBAKFJME
egAwIBEqFABD4gAFX+BT8lg5ixjLNaj+a7CMoZ+XXNmiyo7Ts4ULJudMIorvAYqb6Dv6jmY3fH1vXpM
2sfzClzYPrHB7KTHjBEoAcwBaADAgEAoTkwN6ADAgERoTAELhAA5mBHHHWdu2/OcdDqLMs68DohSYjs
c6TyhN1YElOtMm6gJVhc5uwo2G5XK2UwTKAHMAWgAwIBAKFBMD+gAwIBEKE4BDYYAGyzwsAHmYL93eN
8sPzWEvBXuFMrRuYg4DhFBthYCWPOdb6VRx9ZCbXdSp4RHZY/M1PtN2wwRKAHMAWgAwIBAKE5MDegAw
IBF6EwBC4QAFdl8GPHWYz1wd1aqwH5PwdoQLxUOnyVTalDphHZsNnS7EOcTttENZGl32ks
krbLastPwdChange: 19700101000000Z
krbExtraData:: AAItaaJaZGJfY3JlYXRpb25AU1RDSERQLkNPTQA=
krbExtraData:: AAcBAAIAAnQuQ09NAAA=
objectClass: krbPrincipal
objectClass: krbPrincipalAux
objectClass: krbTicketPolicyAux
dn: krbPrincipalName=kadmin/history@ABC.COM,cn=ABC.COM,cn=kerberos,dc=abc,dc=com
krbLoginFailedCount: 0
krbMaxTicketLife: 86400
krbMaxRenewableAge: 0
krbTicketFlags: 0
krbPrincipalName: kadmin/history@ABC.COM
krbPrincipalExpiration: 19700101000000Z
krbPrincipalKey:: MG6gAwIBAaEDAgEBogMCAQGjAwIBAKRYMFYwVKAHMAWgAwIBAKFJMEegAwIBEq
FABD4gAFY4hn8yhgHzwKY5TbObosMf9OWNXbo27WuB6fuFqbZsNZHTyaipRxXJhHv48pSRnf8BVlcdv
8K+DTKBVQ==
krbLastPwdChange: 19700101000000Z
krbExtraData:: AAItaaJaZGJfY3JlYXRpb25AU1RDSERQLkNPTQA=
krbExtraData:: AAcBAAIAAnQuQ09NAAA=
objectClass: krbPrincipal
objectClass: krbPrincipalAux
objectClass: krbTicketPolicyAux
dn: krbPrincipalName=kadmin/kdcserver@ABC.COM,cn=ABC.COM,cn=kerberos,dc=abc,dc=com
krbLoginFailedCount: 0
krbMaxTicketLife: 10800
krbMaxRenewableAge: 0
krbTicketFlags: 4
krbPrincipalName: kadmin/kdcserver@ABC.COM
krbPrincipalExpiration: 19700101000000Z
krbPrincipalKey:: MIIBTKADAgEBoQMCAQGiAwIBAaMDAgEApIIBNDCCATAwVKAHMAWgAwIBAKFJME
egAwIBEqFABD4gADyFdZ7JiK9Pba54oF0hbjGPYSBq6H+qnM+U8o1oZ33mZ1BAACqEQHOrAt8qDXZYY
UWEfb5y8V6utGc3ejBEoAcwBaADAgEAoTkwN6ADAgERoTAELhAAJT06wv7xrB6z+3+o/wfaILDr2x4U
piJbyfkNWEe1oNJZLjvE9UMIxnfn+wYwTKAHMAWgAwIBAKFBMD+gAwIBEKE4BDYYADAgGFWbWOaeRFS
zKcjTDJMJX4QXV1rCrZEYuE0hcaDTQjCoMXleLiD4uB0LtIqqyarCmOwwRKAHMAWgAwIBAKE5MDegAw
IBF6EwBC4QADjw1CyXbfBBAxJqTkQrLDRwTtzDcJ8IqPVDmTGL1nzMOkNrWz7qlCJnCDkx
krbLastPwdChange: 19700101000000Z
krbExtraData:: AAItaaJaZGJfY3JlYXRpb25AU1RDSERQLkNPTQA=
krbExtraData:: AAcBAAIAAhMIAWlwYWw=
objectClass: krbPrincipal
objectClass: krbPrincipalAux
objectClass: krbTicketPolicyAux
dn: krbPrincipalName=admin/admin@ABC.COM,cn=ABC.COM,cn=kerberos,dc=abc,dc=com
krbPrincipalName: admin/admin@ABC.COM
krbPrincipalKey:: MFagAwIBAaEDAgEBogMCAQGjAwIBAaRAMD4wPKAHMAWgAwIBAKExMC+gAwIBAa
EoBCYIAM4316dUizxrzzChKklYEj+jWWooaIE1pDuORugR4rbQH5DV+w==
krbLastPwdChange: 20180309155715Z
objectClass: krbPrincipal
objectClass: krbPrincipalAux
objectClass: krbTicketPolicyAux
krbLoginFailedCount: 3
krbLastFailedAuth: 20180309155925Z
krbExtraData:: AALbrqJacm9vdC9hZG1pbkBTVENIRFAuQ09NAA==
krbExtraData:: AAgBAA==
dn: ou=people,dc=abc,dc=com
objectClass: top
objectClass: organizationalUnit
ou: people
dn: cn=ud_anwaar,ou=people,dc=abc,dc=com
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
cn: ud_anwaar
sn: ud_anwaar
uid: ud_anwaar
userPassword: abcd1234