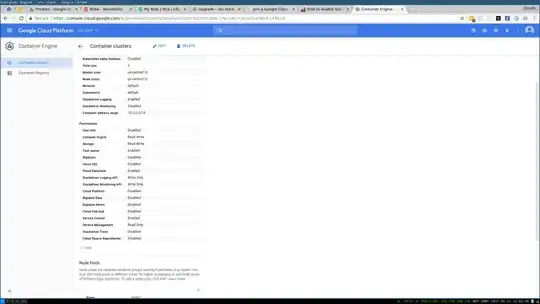
Have a cluster setup with the following permissions.
I tried creating a node pool with new permissions, which seems to be able to enable some things. I didn't find the scope required for stackdriver trace permissions in the documentation located here.
Further, trying to enable monitoring via creating a node pool, and deleting the old one didn't seem to successfully flip the switch.
gcloud container node-pools create pool-2 \
--cluster=cluster-1 \
--scopes=compute-rw,storage-rw,taskqueue,logging-write,monitoring-write,datastore,service-control,service-management