we're currently in the process of putting together our own server Firewall/Router. We were going to use a dedicated solution from someone like Juniper or Watchguard, but it is going to be a lot more cost-effective if we use a server machine we were planning to get already, instead.
About us: We're a website that is going to have two servers behind the Firewall/Router Server (a web server and a database server). All three servers are going to be running Windows Server 2008 R2 x64.
Excuse the crudity of my diagram (I know it's not even close to being technically correct, but it hopefully makes our topology a little clearer)...
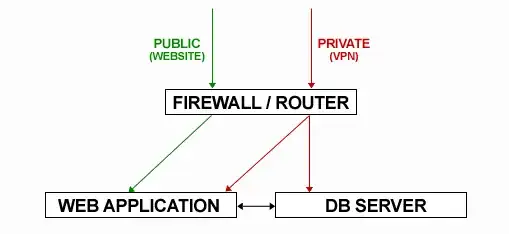
#1 ROUTING
We are using RRAS to configure our routing. At the moment this is configured to give our Web App server internet access (through RRAS's NAT) but I need to set up port forwarding so that any request to port 80 is sent directly to the Web App server.
#2 FIREWALL
Would Windows Advanced Firewall do our required job acceptably? (I imagine the answer to this is yes.)
#3 VPN
Setting up a VPN has been a pain so far (certificates are annoying!). Every tutorial I've seen seems to have a DNS and DHCP roles running on their VPN machine... why is this? Are they both necessary or can I bin them?
Overall
Are the any more tips on how to configure this server for our needs?
Thanks for any advice. I'm sorry if this is a really badly asked question! (There is a bounty, at least :)