Background
I am trying to log in (via SSH, to an Amazon Linux EC2 instance running sssd) as users that I've created in my AWS Directory Services Simple AD. I am authenticating with kerberos and identifying the user with LDAP (all through sssd.)
Problem
I cannot log in as users that I created with adtool, which means that it's much harder for me to automate adding new users to my Simple AD. When I try, KDC says that it can't support the encryption type (I assume this is for the user's password?) See the "Error message" section below.
However, I can log in as both the built-in Administrator user and as users that I've created through the Microsoft Management Console on a Windows Server 2008 EC2 instance joined to the domain. So my setup works, or at least it partially works.
TL;DR solution needed
I need to know what it is that I'm doing wrong with adtool that prevents me from logging in as users created with them. It's not apparent what I am doing wrong and I think this could be generally useful for people trying to do something similar to me. Details below.
Error message
This is the output of sssd when trying to log in as the user created with adtool:
(Thu Dec 31 15:35:35 2015) [[sssd[krb5_child[5459]]]] [sss_child_krb5_trace_cb] (0x4000): [5459] 1451576135.446649: Response was from master KDC
(Thu Dec 31 15:35:35 2015) [[sssd[krb5_child[5459]]]] [sss_child_krb5_trace_cb] (0x4000): [5459] 1451576135.446788: Received error from KDC: -1765328370/KDC has no support for encryption type
(Thu Dec 31 15:35:35 2015) [[sssd[krb5_child[5459]]]] [get_and_save_tgt] (0x0020): 996: [-1765328370][KDC has no support for encryption type]
(Thu Dec 31 15:35:35 2015) [[sssd[krb5_child[5459]]]] [map_krb5_error] (0x0020): 1065: [-1765328370][KDC has no support for encryption type]
(Thu Dec 31 15:35:35 2015) [[sssd[krb5_child[5459]]]] [k5c_send_data] (0x0200): Received error code 1432158209
From the client side it says Permission denied, please try again.
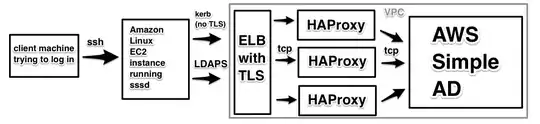
Architecture
Here's what my architecture around the Simple AD looks like:
This setup enables me to use LDAPS even though AWS' Simple AD does not support it.
The route53 record for the ELB is directory.myteam.mycompany.com, but the domain I used for the Simple AD is myteam.mycompany.internal.
Configuration on the machine running sssd
/etc/sssd/sssd.conf:
[sssd]
config_file_version = 2
reconnection_retries = 3
sbus_timeout = 30
services = nss, pam
domains = myteam
[nss]
default_shell = /bin/bash
fallback_homedir = /home/%u
ldap_user_home_directory = unixHomeDirectory
[pam]
reconnection_retries = 3
offline_credentials_expiration = 2
offline_failed_login_attempts = 3
offline_failed_login_delay = 5
[domain/myteam]
enumerate = true
cache_credentials = TRUE
id_provider = ldap
ldap_uri = ldaps://directory.myteam.mycompany.com
ldap_tls_cacert = /etc/pki/tls/certs/ca-bundle.crt
ldap_default_bind_dn = CN=test-user,CN=users,DC=myteam,DC=mycompany,DC=internal
ldap_default_authtok = REDACTED_PASSWORD
ldap_id_use_start_tls = true
ldap_schema = AD
ldap_force_upper_case_realm = true
ldap_id_mapping = true
ldap_search_base = CN=users,DC=myteam,DC=mycompany,DC=internal
ldap_user_uuid = none
ldap_group_uuid = none
chpass_provider = krb5
auth_provider = krb5
krb5_server = directory.myteam.mycompany.com
krb5_realm = MYTEAM.MYCOMPANY.INTERNAL
krb5_changepw_principal = kadmin/changepw
krb5_ccachedir = /tmp
krb5_ccname_template = FILE:%d/krb5cc_%U_XXXXXX
krb5_auth_timeout = 15
krb5_canonicalize = True
/etc/sysconfig/authconfig:
IPADOMAINJOINED=no
USEMKHOMEDIR=yes
USEPAMACCESS=no
CACHECREDENTIALS=yes
USESSSDAUTH=yes
USESHADOW=yes
USEWINBIND=no
PASSWDALGORITHM=sha512
FORCELEGACY=yes
USEFPRINTD=no
FORCESMARTCARD=no
USEDB=no
USELDAPAUTH=no
USEPASSWDQC=no
IPAV2NONTP=no
WINBINDKRB5=no
USELOCAUTHORIZE=yes
USEECRYPTFS=no
USECRACKLIB=yes
USEIPAV2=no
USEWINBINDAUTH=no
USESMARTCARD=no
USELDAP=yes
USENIS=no
USEKERBEROS=no
USESYSNETAUTH=no
USESSSD=yes
USEPWQUALITY=yes
USEHESIOD=no
In addition to these two files, I made sure to enable password authentication in sshd_config and enabled sssd in the pam modules with sudo authconfig --updateall --enablesssd --enablesssdauth.
/etc/pam.d/system-auth:
auth required pam_env.so
auth sufficient pam_unix.so nullok try_first_pass
auth requisite pam_succeed_if.so uid >= 500 quiet_success
auth sufficient pam_sss.so use_first_pass
auth required pam_deny.so
account required pam_unix.so
account sufficient pam_localuser.so
account sufficient pam_succeed_if.so uid < 500 quiet
account [default=bad success=ok user_unknown=ignore] pam_sss.so
account required pam_permit.so
password requisite pam_pwquality.so try_first_pass local_users_only retry=3 authtok_type=
password sufficient pam_unix.so sha512 shadow nullok try_first_pass use_authtok
password sufficient pam_sss.so use_authtok
password required pam_deny.so
session optional pam_keyinit.so revoke
session required pam_limits.so
-session optional pam_systemd.so
session optional pam_mkhomedir.so umask=0077
session [success=1 default=ignore] pam_succeed_if.so service in crond quiet use_uid
session required pam_unix.so
session optional pam_sss.so
Software versions
uname -a:Linux ip-172-31-31-2 4.1.10-17.31.amzn1.x86_64 #1 SMP Sat Oct 24 01:31:37 UTC 2015 x86_64 x86_64 x86_64 GNU/Linuxsssd1.12.2adtool1.3.3openldap-clients2.4.23-34.25.amzn1
Differences between the users
To show how these users differ in my directory, here is the output of querying them with ldapsearch from the instance running sssd.
User created with adtool (edit: you'll see below that the pwdLastSet value is present, I believe this was not present earlier and its presence is the key to my answer):
$ ldapsearch -LLL -H ldaps://directory.myteam.mycompany.com -D CN=Administrator,CN=users,DC=myteam,DC=mycompany,DC=internal -x -W '(cn=test-user)'
Enter LDAP Password:
dn: CN=test-user,CN=Users,DC=myteam,DC=mycompany,DC=internal
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: test-user
instanceType: 4
whenCreated: 20151230204358.0Z
displayName: Test user
uSNCreated: 3532
name: test-user
objectGUID:: ZhfGzcqLd06x2UBU3UNiZQ==
codePage: 0
countryCode: 0
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAHWfr9xoaXwKvEcuoUwQAAA==
accountExpires: 9223372036854775807
sAMAccountName: test-user
sAMAccountType: 805306368
userPrincipalName: test-user@myteam.mycompany.internal
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=myteam,DC=mycompany,DC
=internal
userAccountControl: 512
lockoutTime: 0
whenChanged: 20151231150317.0Z
uSNChanged: 3619
pwdLastSet: 130960477970000000
distinguishedName: CN=test-user,CN=Users,DC=myteam,DC=mycompany,DC=internal
User created through the Microsoft Management Console:
$ ldapsearch -LLL -H ldaps://directory.myteam.mycompany.com -D CN=Administrator,CN=users,DC=myteam,DC=mycompany,DC=internal -x -W '(sAMAccountName=test-windows-2008)'
Enter LDAP Password:
dn: CN=Test User,CN=Users,DC=myteam,DC=mycompany,DC=internal
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: Test User
sn: User
givenName: Test
instanceType: 4
whenCreated: 20151230223533.0Z
whenChanged: 20151230223534.0Z
displayName: Test User
uSNCreated: 3563
uSNChanged: 3563
name: Test User
objectGUID:: 2cuynP3/9EeRIm1fCUJ9jA==
userAccountControl: 512
codePage: 0
countryCode: 0
pwdLastSet: 130959885340000000
primaryGroupID: 513
objectSid:: AQUAAAAAAAUVAAAAHWfr9xoaXwKvEcuoVwQAAA==
accountExpires: 9223372036854775807
sAMAccountName: test-windows-2008
sAMAccountType: 805306368
userPrincipalName: test-windows-2008@myteam.mycompany.internal
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=myteam,DC=mycompany,DC
=internal
distinguishedName: CN=Test User,CN=Users,DC=myteam,DC=mycompany,DC=internal