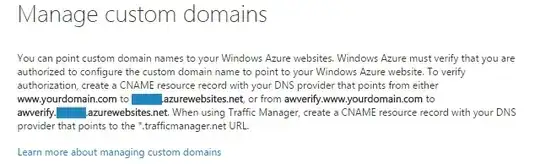
Let me try to answer your question by providing two cases. In both cases, you will still need to verify that you are the owner, it is just a security step.
1) www.example.com is not being visited and not in production
2) www.example.com is currently in production and is heavily being used
1) If your domain is now being setup or is not in production/being accessed, you can create a CNAME record that points to yoursite.azurewebsites.net. No awverify.myhost.azurewebsites.net needed.
2) If your domain is in heavy use and being accessed currently, and you wish to test to see if Azure sees the changes in your DNS records, you can create a sub-domain named 'awverify' as in awverify.example.com and point it to a created sub-domain awverify.myhost.azurewebsites.net. This will not affect your current users accessing your website going to www.example.com. Once Azure verifies that it sees the change in the CNAME, you can then notify users of maintenance and change the A record. If you just change the A record, the site may be seen as offline for up to 8 hours.
So to answer your question simply, you don't need to use awverify. Just changing the CNAME can work as well. Also, just changing the A record will redirect all traffic from yourdomain.com to yoursite.azurewebsites.net
Hope this helps.