I'm working on setting up a lab environment with two Windows Server (virtual) machines that cooperate in an AD FS configuration.
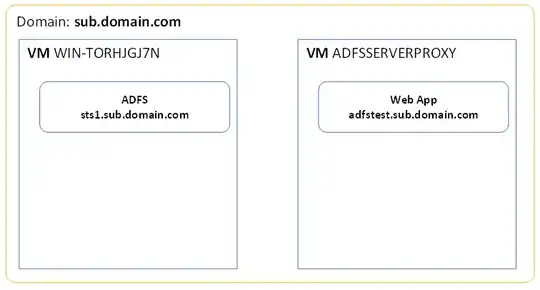
- WIN-TORHJGJ7N: Windows Server 2012, running AD FS 2.0. Also the domain controller.
- ADFSSERVERPROXY: Despite its name, not really set up as a proxy (yet). Most importantly, it contains a web application running on
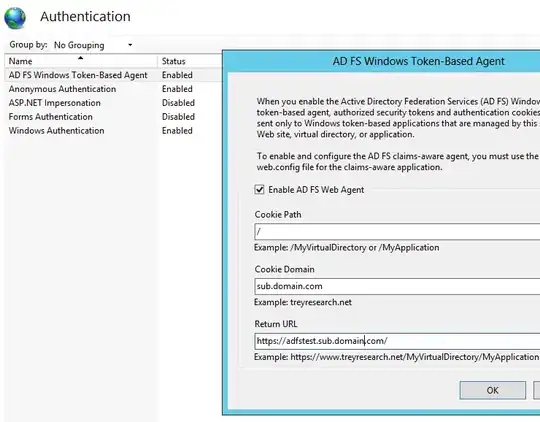
https://adfstest.sub.domain.com/. It is protected with AD FS Windows Token-Based Agent, as shown on the below image. The web application is a simple "hello world" program, so no authentication logic on that side whatsoever.
On my first machine, I want to configure my Relying Party Trust, but I'm having trouble configuring my endpoints. I tried http://sts1.sub.domain.com/adfs/ls/, http://adfstest.sub.domain.com/ and other variations, but really I'm just not sure what is intended to go there. Is it an arbitrary value, or does it need to point to a specific location? If it should point to my web application, do I need to implement authentication logic at the application?
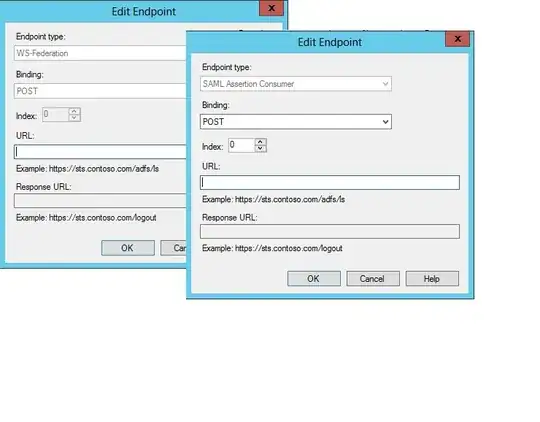
So, cutting a long story short: what is expected to be the relying party trust endpoints in this setup?
EDIT:
One of the errors I get when I point the endpoint to an arbitrary url on the application side (https://adfstest.sub.domain.com/), is the following:
The AD FS Web Agent for Windows NT token-based applications encountered a serious error. The cookies that were presented by the client could not be validated.
This condition occurs when a client presents well-formed cookies that are not valid. If the client is known to be a valid user, this error might be caused by a transient issue. For instance, trust properties (for example, certificates) may have changed recently or revocation status may not be available from the certification authority.
User Action Look for additional events in the security log that may contain more details. Consider enabling failure auditing on this Web server if auditing is not already enabled.