I created a new Windows instance on AWS EC2, using a keypair I created by uploading my public key from my local machine.
The instance launched fine, but it won't decrypt the password. It reports:
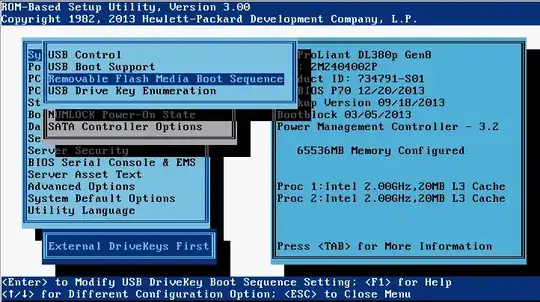
I'm certain I uploaded the correct key. I've verified that the fingerprints match with the weird fingerprint format AWS uses. But it just won't decrypt.
I've tried uploading the key file, and pasting it into the form.
I eventually figured out that it isn't stripping the trailing newline, and deleted the blank line in the key. That just gets me to a new error when I click "Decrypt Password", though: