Tl;Dr:
How do I stop chrome from refusing to load pages that are blocked by OpenDNS, where the server has explicitly requested HTTPS?
Long question:
I have a large problem with Chrome in my organisation. I use DNS to manage web site blocking, for sites which are not appropriate and are potentially a risk to the organisation where I do this.
I only want to use Chrome over the network, as Internet Explorer has compatibility problems with some sites that we use (We cannot change this either or use different sites). Therefore using internet explorer is not a solution.
I do not want to install a different browser, for multiple reasons. Mainly because of the difficulty of rewriting the customised add-ons that we use.
However, recently, I have had lots of problems with Chrome SSL Errors. I cannot use my custom OpenDNS block pages, which uses the contact form to request an unblocking.
Chrome often blocks OpenDNS for sites (a good example is Facebook) that request HTTPS. Some sites like https://internetbadguys.com (OpenDNS example) This means that chrome refuses to load the blocking page, explaining that the site is blocked. Instead they often call IT support, but they want a solution, as they are sick of getting lots of SSL errors.
I have tried looking into ways to turning this off. I have tried:
- Typing "proceed". That didn't work.
- Typing "proceed", pressing enter. Didn't work
- I cannot find phishing and anti-malware any more in Chrome, from the internet guides.
- Not using HTTPS. However there is an automatic redirect to HTTPS on most sites. Therefore the error keeps coming up.
- Checking my clocks. They were correct.
Does anyone have an idea on how to disabling, bypassing or working around this "feature"?
EDIT: This is an example what I am talking about -
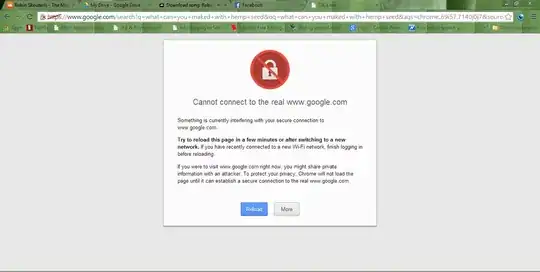 I found that on google images.
I found that on google images.
NOTE: I DO NOT block Google.
EDIT 2: My clocks are correct. I cannot stop using OpenDNS either.