I've setup a basic group policy consisting of the default Applocker rules. Per Microsoft's technet article on the subject, any files not explicitly allowed to run by the policy are supposed to be blocked from running. After deploying this policy and verifying it was being applied to the correct user using gpresult, I was still able to download and run an exe from the internet, an exe that was saved to the user profile's temp folder. It was at that point I did more googling, and saw that the App Identity service had to be running, and it wasn't: So, like any good admin, I started it, set it to automatic, and rebooted just in case. The policy still didn't work after restarting. Below is a screenshot of the current policy.
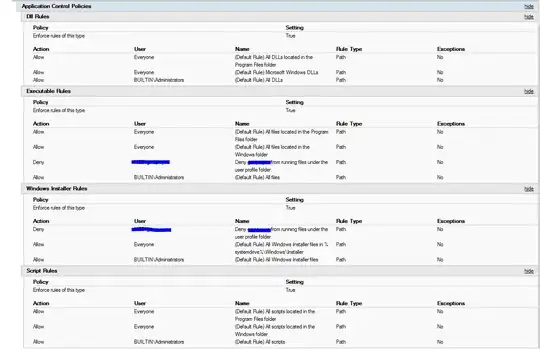
I added the deny rules explicitly because the default rules weren't working. I correctly applied the policy to the machine and verified that the rules are enforced (it says so in the screenshot). I used the Test-AppLockerPolicy cmdlet to verify that the rule is should be blocking the EXEs and MSIs from running, but it doesn't. Open to most suggestions, no matter how ludicrous they may sound.
Update
Forgot to add that I checked the event log for AppLocker during this whole fiasco, and it was blank. Not a single entry the entire time.