I have a Draytek 3200 router and a pfsense rackmount router that I am trying to get to route to each other.
I have a subnet on each router and a subnet for the link between, as shown here:
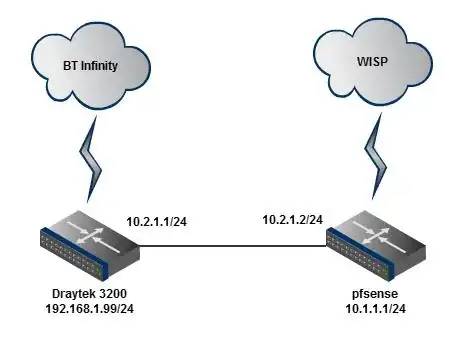
As it stands at the moment I can ping from the Draytek 192.168.1.0/24 subnet to 10.2.1.2/24 successfully. I can ping from 10.2.1.1 to 10.2.1.2. I can't ping from the pfsense at all to the draytek's 192.168.1.0/24 subnet.
Ultimatly I am trying to be able to ping anything on the 192.168.1.0/24 subnet from any LAN on the pfsense.
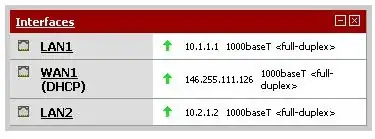
Current pfsense Interfaces
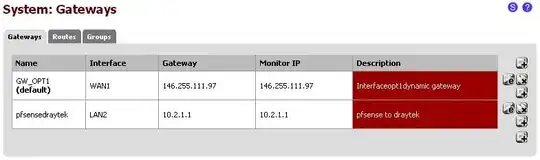
Current pfsense Gateways
Current pfsense Routes
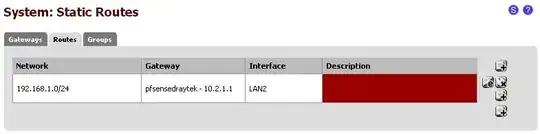
I've allowed everything through on the firewall, as far as I can tell.
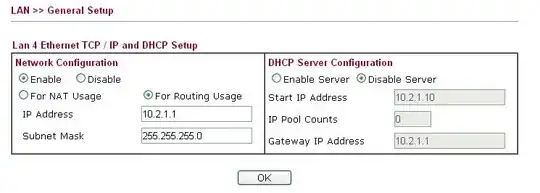
Draytek Subnet Configuration
Draytek Static Routes
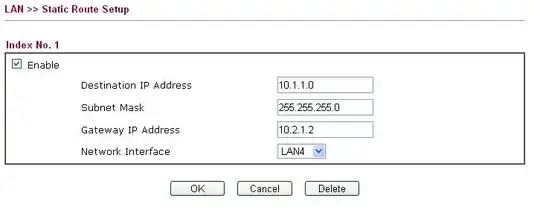
I'm certain I'm missing something and it's probably obvious, but I can't for the life of me get this working.
Draytek Routing Table
Key: C - connected, S - static, R - RIP, * - default, ~ - private
* 0.0.0.0/ 0.0.0.0 via 81.142.64.1 WAN1
S 10.1.1.0/ 255.255.255.0 via 10.2.1.2 LAN1
C 10.2.1.0/ 255.255.255.0 directly connected LAN4
* 81.142.64.1/ 255.255.255.255 via 81.148.64.1 WAN1
C~ 192.168.1.0/ 255.255.255.0 directly connected LAN1
S~ 192.168.2.0/ 255.255.255.0 via 86.143.86.52 VPN-3
S~ 192.168.3.0/ 255.255.255.0 via 146.255.106.220 VPN-1
S~ 192.168.4.0/ 255.255.255.0 via 146.225.121.125 VPN-5
S~ 192.168.5.0/ 255.255.255.0 via 217.42.42.188 VPN-4
S~ 192.168.6.0/ 255.255.255.0 via 86.22.102.129 LAN3
C 192.168.20.0/ 255.255.255.0 directly connected DMZ
S 217.32.42.177/ 255.255.255.255 via 217.32.42.177 WAN1
C 217.32.47.176/ 255.255.255.240 directly connected LAN1
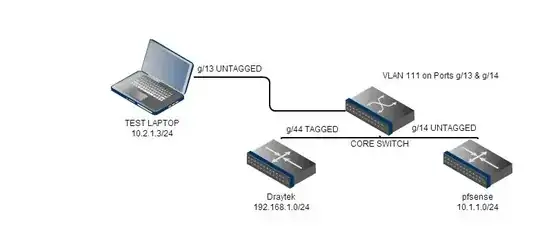
I wasn't sure if it's relevant but the two routers are not directly connected via a patch cable as the Draytek only has one true LAN port. The LAN 4 on the Draytek is tagged, passed to a switch which is set to untagged on the port the pfsense is connected to.
PFSense Firewall Log
Firewall Logs
ACT IF Source Destination Prot
X LAN2 10.2.1.2:80 10.2.1.1:3439 TCP:FA
X LAN2 10.2.1.2:80 10.2.1.1:39437 TCP:FA
X LAN2 10.2.1.2:80 10.2.1.1:39441 TCP:FA
X LAN2 10.2.1.2:80 10.2.1.1:39445 TCP:FA
Core Switch VLAN Config