There is a principal that could achieve this (USERS)
click on change user and type (USERS), see below
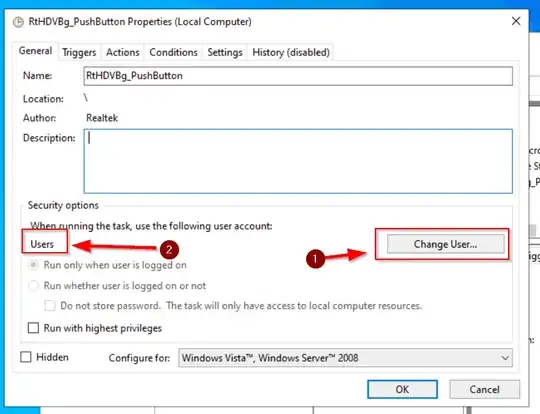
If you actually export this task with the USERS Principal to its RAW XML output using command line you will see the following
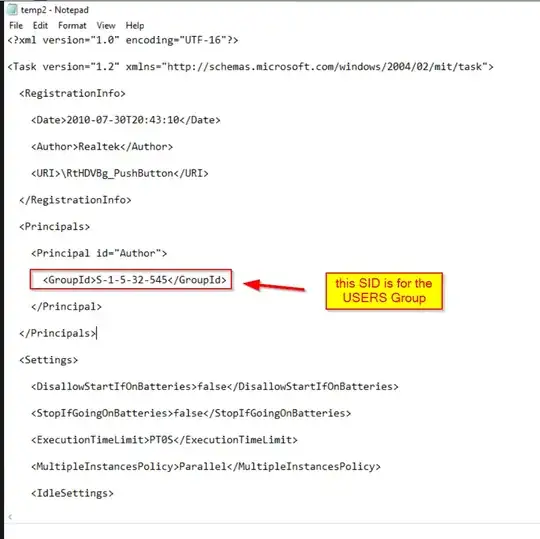
S-1-5-32-545
The Group ID is the secret sauce here and is what determines the security context under which the task will run
There are other principals that use well known SIDs as well (SYSTEM and INTERACTIVE)
I would recommend for good understanding of SIDs in Windows to read https://docs.microsoft.com/en-US/windows/security/identity-protection/access-control/security-identifiers
and then a good understanding of interfacing with Task Scheduler using Command line and Custom XML files in addition to the GUI
https://www.scriptjunkie.us/2013/01/running-code-from-a-non-elevated-account-at-any-time/

