Possible Duplicate:
How do I deal with a compromised server?
One of our desktop machines (Win 7 64 bit) has recently been complaining of slow down, particularly when accessing resources on a SBS2003 server (also a DC). One thing I looked into was the AV on the server, which was taking ~500MB RAM (it only has 4GB) so I've tackled that. There are still issues, and in addition to this I took a packet capture on the server.
The desktop (23 in the image below) keeps making loads and loads of SMB requests to the server, even though consciously the user isn't accessing any resources. Additionally, it randomly tries to logon to the server with another user's credentials, for no good reason. The credentials don't even show up in the credential manager on the machine.
Why is this happening? I've had a quick Google and can't find much on the subject - worryingly one of the only things I could find when searching for 'nt create andx request' was a whitepaper titled 'Microsoft LSASS Buffer Overflow from exploit to worm.' Hope it's nothing along those lines, what can I do to further get to the bottom of this? If it's any help using netstat and taskmgr on the client I've determined that the process responsible for this was called something like 'NT Kernel and System'.
The Win 7 machine is still painfully slow, and no other desktops have been affected. We don't have a system restore going back very far, so likely will just wipe it and start again. I have an image of the packet capture of the client querying the server, with someone else's credentials, and this again loops over and over. The items I've blanked out in image 2 are: from client(red): computer name and user name(someone else's); from server (blue): domain name (full), server name, domain name (shortened), server, username. 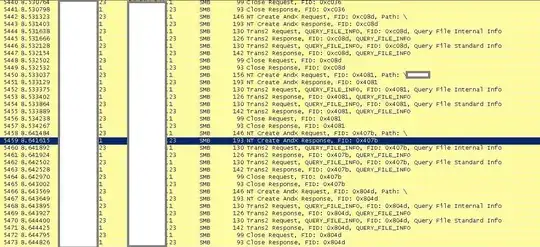
Edit: a virus scan on the Win 7 desktop, using ESET NOD32 Ver 5, has found Java/Exploit.CVE[DATE].BR trojan. It's cleaned/deleted the file, how worrying is this? Should we re-build machine to be safe?