Given:
- A VM running Windows 2008
- I am logged on there using my domain account (SHUNRANET\markk)
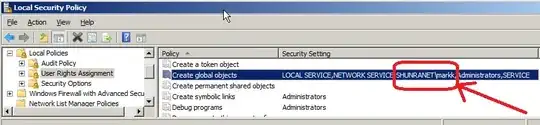
- I have added the "Create global objects" privilege to my domain account:
- The VM is restarted (I know logout/logon is enough, but I had to restart)
- I logon again using the same domain account. It seems still to have the privilege:
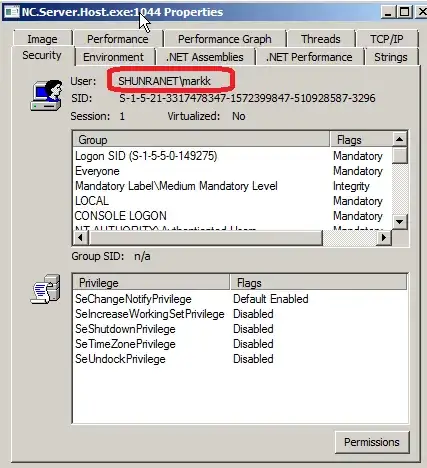
- I run some process and examine its Security properties using the Process Explorer. The account does not seem to have the privilege:
This is not an idle curiousity. I have a real problem, that without this privilege the named pipe WCF binding works neither on Windows 2008 nor on Windows 7! Here is an interesting discussion on this matter - http://social.msdn.microsoft.com/forums/en-US/wcf/thread/b71cfd4d-3e7f-4d76-9561-1e6070414620.
Does anyone know how to make this work? Thanks.
EDIT
BTW, when I run the process elevated, everything is fine and the process explorer does display the privilege as expected:
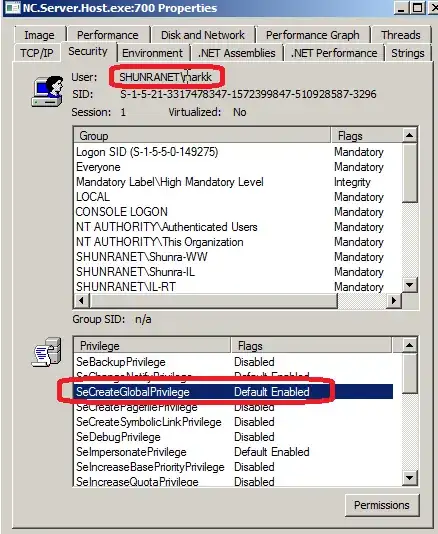
But I do not want to run it elevated.
EDIT2
I equally welcome any solution. Be it configuration only or mixed with code.
EDIT3
I have posted the same question on MSDN forums and they have redirected me to this page - http://support.microsoft.com/default.aspx?scid=kb;EN-US;132958. I am yet to determine the relevance of it, but it looks promising.
Notice also that it is a completely coding solution that they propose, so whoever moved this post to the ServerFault - please reinstate it back in the StackOverflow.