I am trying to reach an on-premise machine (let's call it exovie) from Google Cloud Run via the Serverless VPC Connector.
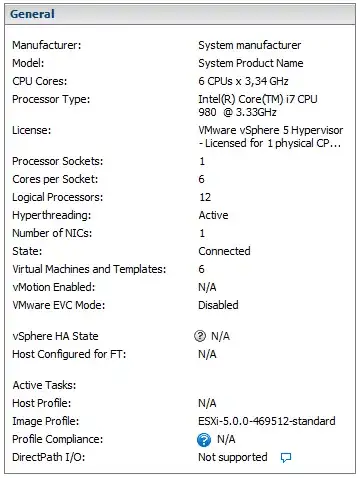
Simplified network configuration
This is how the network is configured:
- The VPC is connected to our on-premise network
172.20.0.0/20using a Google Cloud VPNexoscale-at-vie-1-tunnel.
My application
train-graphqlis deployed on Cloud Run (fully managed, europe-west6) and is attempting to access theexovieVM via a Serverless VPS Connectoreuw6-connector(also europe-west6, network:10.94.0.0/28).Routes are published to a Cloud Router.
I also have a
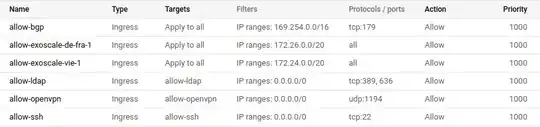
servicessubnetwork10.172.10.0/24used by some Google Cloud Compute Engine VMs which hosts a LDAP server (opendldap-server,10.172.10.2).There is no special restrictive firewall rules:
Connectivity tests
- I start a SSH session from the
openldap-serverat10.172.10.2toexovieat172.24.0.20. - My application
train-graphqlis connected to theopenldap-serverat10.172.10.2via the Serverless VPC Connectoreuw6-connectorwithout issues. - A connectivity test on port 22 from the first instance of the Serverless VPC Connector
euw6-connectorat10.94.0.2toexovieat172.24.0.20is successful.
Final thoughts
Since I can SSH from Cloud Run to Compute Engine and from Compute Engine to exovie, a via solution could be to use a Compute ENgine VM as proxy to achieve this connection, but it sounds like a dirty hack.