I thought it would be a good idea to setup MX records in one zone, while using another zone managed by Terraform (using GCP) to deal with A records and CNAMES for the web server I'm setting up. Both zones have the sane DNS name (e.g. "example.com.")
I ended up with two different sets of NS records to configure as nameservers for the domain, so I added 2 servers from the first and two from the second, meaning:
- ns-cloud-c1.googledomains.com
- ns-cloud-c2.googledomains.com
- ns-cloud-d1.googledomains.com
- ns-cloud-d2.googledomains.com
Nameservers c1-c4 contain the MX records with the DNS zone that is not managed by Terraform, whereas nameservers d1-d4 contain the A and CNAME records managed by Terraform.
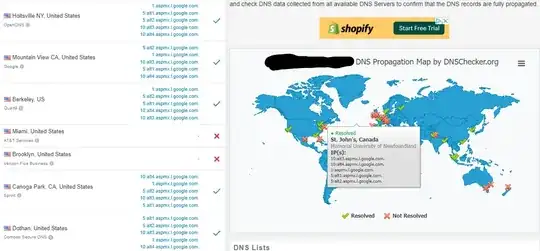
As I checked for propagation with https://dnschecker.org/, I ended up with some funky behavior, where every refresh gives me different results, and never fully propagated.
A few refreshes for the A record:
Refresh #1
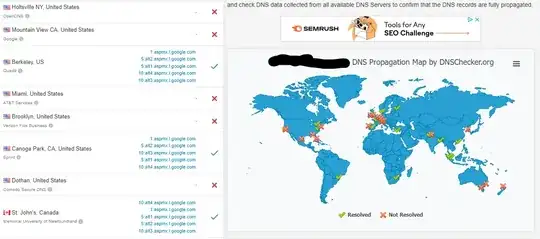
 Refresh #2
Refresh #2
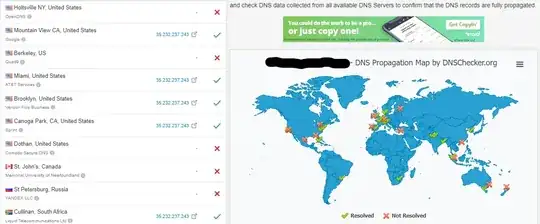
 Refresh #3
Refresh #3
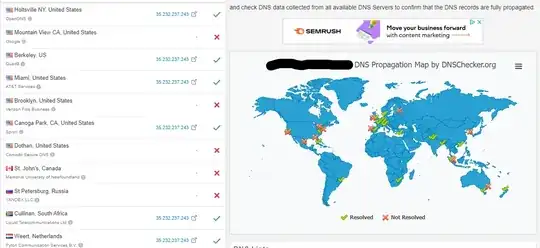
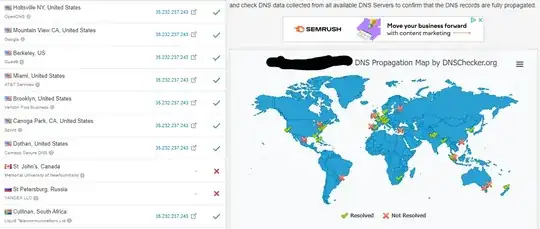
And for the MX records
My goal is to have a DNS zone for "example.com" that is fully managed by Terraform (for A and CNAME records) so that it can be destroyed without affecting the MX records. My questions are:
Why does this behavior happen?, meaning, getting records not resolved on half of the propagation, but then appearing resolved on the next refresh.
Should I be associating my domain name with multiple NS records in separate zones? (e.g. ns-cloud-[cde][1234].googledomains.com)
3.- Can I have 1 zone point to another one so that my DNS records are sharDed somehow? and just configure a single set of NS records with my domain.
4.- What is the best practice when it comes to using multiple zones for the same domain (not talking about subdomains)