I'm having trouble exposing ports on my ECS Fargate containers.
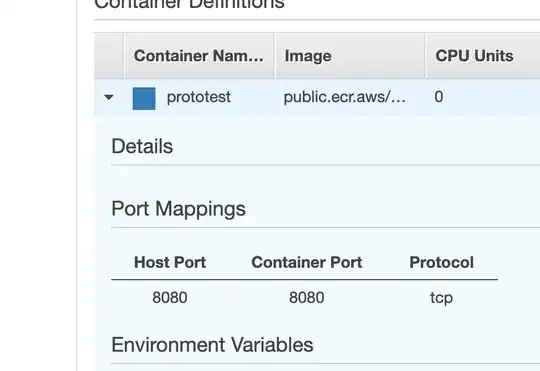
I have applied port mapping on container level for my task definition, like so:
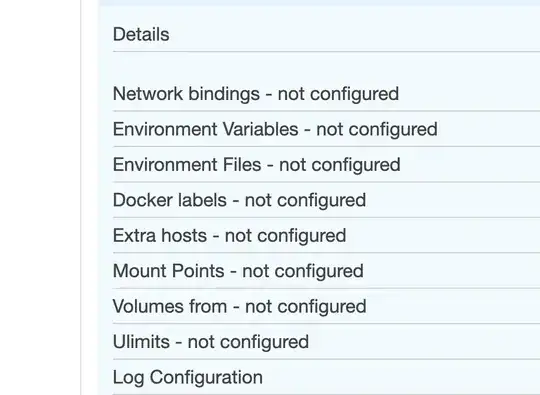
On the containers themselves, it looks like there is no specific mapping enabled, or am I reading this wrong?
The containers need to intercommunication with each other (Clustered software)
I fetch the IP from the meta container configuration per container, e.g.
"Networks": [
{
"NetworkMode": "awsvpc",
"IPv4Addresses": ["172.31.22.46"],
In this case, 172.31.22.46:8080 should be open for communication, within the ECS cluster. That does however not happen. the endpoints are unreachable and nodes cannot communicate.
Are there more things I need to do to allow this to work? e.g. open up some security setting somewhere?
Sorry for the fairly cryptic question, but I don't know how to explain this better.