I am currently in the process of migrating an old webserver.
The old server uses basic auth with users stored in a mysql table and mod_auth_mysql enabled.
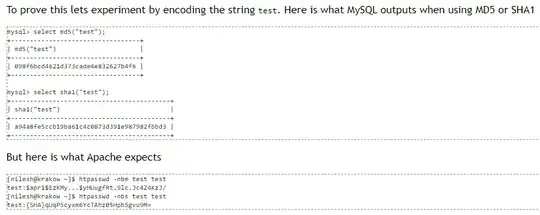
The password ist stored with apaches build in sha1 function SELECT sha1('secret') which works for mod_auth_mysql
Unfortunately mod_auth_mysql is not supported anymore. That's why I found mod_authn_dbd as an alternative.
https://documentation.help/httpd-2.4-es/mod_authn_dbd.html
I alreay managed to get everything up and running until the point that I can login with basic auth and a fixed password
<Location />
AuthType Basic
AuthName "Test"
AuthBasicProvider dbd
Require valid-user
AuthDBDUserPWQuery "SELECT '{SHA}qUqP5cyxm6YcTAhz05Hph5gvu9M=' FROM users WHERE user = %s"
</Location>
I only store the sha1 hash in the user table. While the old mod_auth_mysql accepted hashes generated by mysql (SELECT sha1('test')=a94a8fe5ccb19ba61c4c0873d391e987982fbbd3) mod_authn_dbd doesn't.
According to https://documentation.help/httpd-2.4-es/password_encryptions.html
SHA1 "{SHA}" + Base64-encoded SHA-1 digest of the password.
Passwords generated by htpasswd are accepted.
htpasswd -bns user test
user:{SHA}qUqP5cyxm6YcTAhz05Hph5gvu9M=
Now I need to convert this value a94a8fe5ccb19ba61c4c0873d391e987982fbbd3 (stored in my db for password test) to qUqP5cyxm6YcTAhz05Hph5gvu9M= (accepted value for password test) inside mysql
I already tried
SELECT to_base64(sha1('test')), to_base64(ucase(sha1('test'))), to_base64(lcase(sha1('test')));`
but none produces the expected results.
I either need a way to convert my existing password hashes to the expected format or convince mod_authn_dbd to accept my existing sha1 hash.
Any help would be appreciated