A public-key infrastructure (PKI) is a set of hardware, software, people, policies, and procedures needed to create, manage, distribute, use, store, and revoke digital certificates. In cryptography, a PKI is an arrangement that binds public keys with respective user identities by means of a certificate authority (CA). There are three main categories of PKI: Web / SSL certs, corporate networks, and Government ID / ePassport.
Overview
The term "public-key infrastructure (PKI)" is an umbrella term to cover many different aspects of the backbone that underpins the system of digital certificates issued by a Certificate Authority. The term PKI contrasts with web-of-trust, which is a competing system for establishing the trusted identity of a key holder.
Here at security.stackexchange.com, we accept questions on all aspects of PKI, from conceptual overview, to software implementation, to practical concerns, to organizational policies.
Technical
As its most basic, a PKI is a single certificate authority - a public/private key pair included in a self-signed root certificate, which it uses to sign certificates for end-users; and the clients which consume those certificates.
In practice, real-world deployments of PKIs use several layer of CAs for both security and organizational reasons.
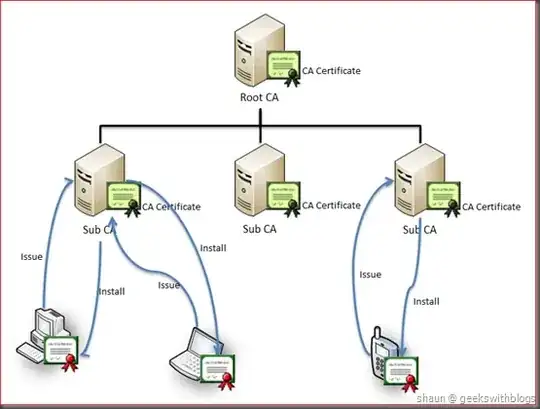 (image credit: "Working with Active Directory Certificate Service via C#"
(image credit: "Working with Active Directory Certificate Service via C#"
Data Format Standards
Generally speaking all certificates use the x509 standard for the data format, though the Extended Access Control (EAC) format is used for certificates embedded in the chips of electronic passports.
Policy
In addition to the technical requirements of having a self-signed root cert, a Certificate Authority needs to follow a number of strict operational and auditing standards in order to be included in the list of publicly trusted root CAs. For example, here are the lists of root CAs trusted by iOS and Firefox.
The rules of conduct for CAs is maintained by the CA/Browser Forum (CAB). According to wikipedia/CA/Browser_Forum, the CA/Browser forum is:
is a voluntary consortium of certification authorities, vendors of Internet browser software, operating systems, and other PKI-enabled applications that promulgates industry guidelines governing the issuance and management of X.509 v.3 digital certificates that chain to a trust anchor embedded in such applications.