My company's set-up involves a single AP (TPlink) that is configured to authenticate clients using RADIUS. All works well, but: on a regular WPA/WPA2 network, once you have the PSK, you are able to decode all the traffic other users generate. On an IEEE 802.1X - WPA2, according to this, a key is generated for each user separately, so, at least in theory, it should not be possible to decode traffic of another client station using a different set of credentials. However, I have read a few posts on various forums claiming that this is not the case, and that in fact, once you are authenticated using any user/password pair, you can decode all traffic. Can someone clarify this for me? Can someone elaborate?
-
1Some security issues and ways to prevent them are explained in [rfc3579](https://tools.ietf.org/html/rfc3579#section-4.1) – BadSkillz May 07 '15 at 11:38
2 Answers
802.1X is NOT an encryption type. It is basically just a per-user (e.g. username and password) authentication mechanism.
WPA2 is a security scheme that specifies two main aspects of your wireless security:
- Authentication: Your choice of PSK ("Personal") or 802.1X ("Enterprise").
- Encryption: Always AES-CCMP.
If you're using WPA2 security on your network, you have two authentication choices: You either have to use a single password for the whole network that everyone knows (this is called a Pre-Shared Key or PSK), or you use 802.1X to force each user to use his own unique login credentials (e.g. username and password).
Regardless of which authentication type you've set up your network to use, WPA2 always uses a scheme called AES-CCMP to encrypt your data over the air for the sake of confidentiality, and to thwart various other kinds of attacks.[Ref]
So when the system use AES-CCMP, which user with which username/password has the key of the AES encryption?
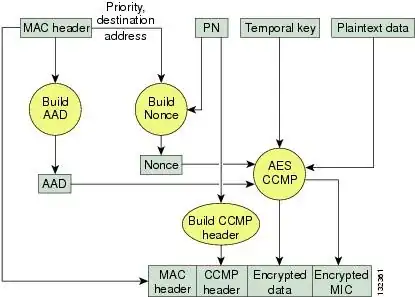
It means after that each user is authenticated, the system encrypts all traffic with temporal 128-bit key and AES.
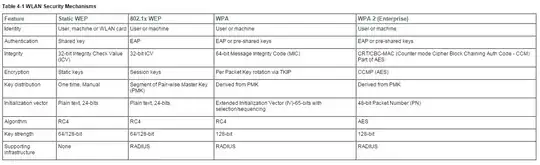
WPA is an 802.11i-based security solution from the Wi-Fi Alliance that addresses the vulnerabilities of WEP. WPA uses Temporal Key Integrity Protocol (TKIP) for encryption and dynamic encryption key generation by using either a pre-shared key, or RADIUS/802.1x-based authentication. The mechanisms introduced into WPA were designed to address the weakness of the WEP solution without requiring hardware upgrades. WPA2 is the next generation of Wi-Fi security and is also based on the 802.11i standard. It is the approved Wi-Fi Alliance interoperable implementation of the ratified IEEE 802.11i standard. WPA 2 offers two classes of certification: Enterprise and Personal. Enterprise requires support for RADIUS/802.1x-based authentication and pre-shared key (Personal) requires only a common key shared by the client and the AP.
the key exchange will be done by using PMK(Pairwise Master Key) and EAP-TLS
Key Management for Link Layer Security Key Management for Link Layer Securit
Cisco Unified Wireless Network Architecture—Base Security Features
-
So let me clarify that. You say that the key is the same for all stations? – Konrad Gajewski May 07 '15 at 12:01
-
-
1Okay, AES-CCMP for the session. But where does the session key come from? How does that session key exchange work? Is Diffie-Hellman involved? How is that session key exchange authenticated (if at all)? – StackzOfZtuff May 07 '15 at 12:30
-
@StackzOfZtuff by using PMK(Pairwise Master Key) that it uses EAP-TLS ... http://www.ieee802.org/1/files/public/docs2004/AFjul04KimKey_Management_For_Link_Layer_Security.pdf – Ali May 07 '15 at 12:50
-
So... AFAIU the username/password from 802.1x does not get into the exchange and/or generation of the keys. Am I right? – Konrad Gajewski May 07 '15 at 17:23
-
@KonradGajewski yes it is true. the system uses other methods for generating temporal keys.and user/pass just use for authentication, and not for encryption, therefore encryption keys of each user for traffics are different. – Ali May 08 '15 at 03:45
-
@Ali. Thanks, it's getting a bit mor clear now. But: in Wireshark you are able to decode dumped traffic of a WPA2 session provided you have the key. However the Enterprise version is still not available. How come? (Yes, I know, I should ask the guys that develop Wireshark, but what are your thoughts about it? – Konrad Gajewski May 08 '15 at 08:51
You should be more worried about rouge access points and de-auth attacks not the encryption on your access point.
The encryption on WPA2 is pretty secure, so hackers generally don't attack it. Instead hackers usually will try to get the client to connect to a rouge (evil) access point that they control. If they can get a person to connect to the rouge access point they get two things
- Credentials when the user tries to authenticate. (If you are using PEAP or WPA2/Personal)
- Ability to capture and control all traffic for clients connected to rouge access point.
Hackers can use stolen information from #1 to connect to your real access point and have access to your network. They can use #2 to steal more information from the client.
You can mitigate both of these issues. First you should require two factor authentication. You can use EAP-TLS to take care of that, but it is complicated to setup and distribute the client certificates needed. If you use PEAP, you can still have a second factor by using Google Authenticator (GA). GA will work on any RADIUS server that supports PAM. Instructions for FreeRadius are here. That way any stolen passwords will not be usable after 30 seconds. Never use a pre-shared key (WPA2/Personal WPA2/PSK) on a network with sensitive information. We only use WPA2/PSK for guest networks that access the Internet only.
Mitigating the second issue is all about client configuration and user education. First, educate your users never to attached to a wireless network they don't recognize. Evil access points will often use the same SSID as your access point so client configuration is important. If you are using EAP-TLS then you are pretty safe, but most people opt for PEAP instead because configuring and distributing the client certificates needed for EAP-TLS is hard. If you are using PEAP, you can setup the client to only accept certain server certificates. Most people skip this step but it is very important. Instructions for Windows 7 using PEAP are here. Notice in step 9 that you can configure the client to only accept certain certificates. It is not enabled by default, but you should always enable it.
- 127
- 1
-
1
-
Sorry. The question was about the security of IEEE 802.1X. In my opinion the configuration and implementation of EAP and RADIUS are the weak points, not the keys. – kheld May 07 '15 at 18:21
-
1No. The question was if the username/password pair influence the encryption. – Konrad Gajewski May 07 '15 at 18:44
-
In other words if I give someone guest access, will they be able to sniff the traffic form then on. – Konrad Gajewski May 07 '15 at 19:02