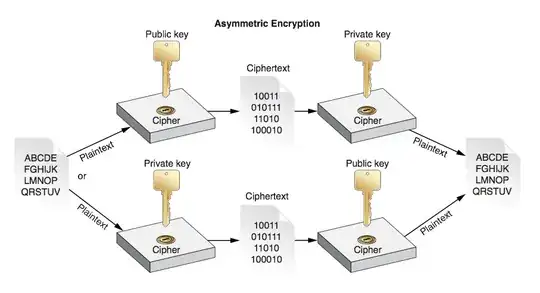
Above picture is captured from iOS Security overview at page 25. The path encrypt with public and decrypt with private makes sense. But the other path, encrypt with private and decrypt with public to recreate plain text is something i am not able to understand. If it is just for integrity check, then that should be fine since we will be only worried about tampering. But if the secrecy of the text should be maintained, shouldn't this pose a problem when decrypt with public key?
Can someone help me understand how this path is still secured?