At home, I have a simple ISP supplied router where I have set up a WPA2-PSK wireless network for our laptops and other devices. While I played around with Wireshark, I noticed that I could use my laptop to see what my tablet is doing in the internet, without the tablet noticing anything.
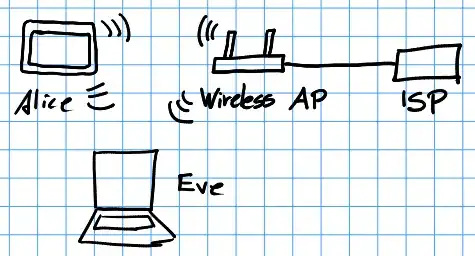
I think this works because all devices have the same wireless key and there is no way to send packages to one recipient. The recipients are usually kind enough to ignore all the packages that are not addressed to them.
When people visit, I will give them the key since I do trust them enough to perform illegal activities (at least knowingly) or eavesdrop on my traffic. However, they could technically. I came up with the extreme case where Eve would take an old smartphone, enter the key of Alice's network and charge that behind some furniture. It would record parts of the traffic (like DNS requests and passwords in HTTP) and sent it to some server. Alice would not notice this, and even if she finds the phone, Eve could say that she just forgot that she charged the phone there.
Would setting up WPA2-Enterprise mitigate this sniffing problem, at least across the different identities?