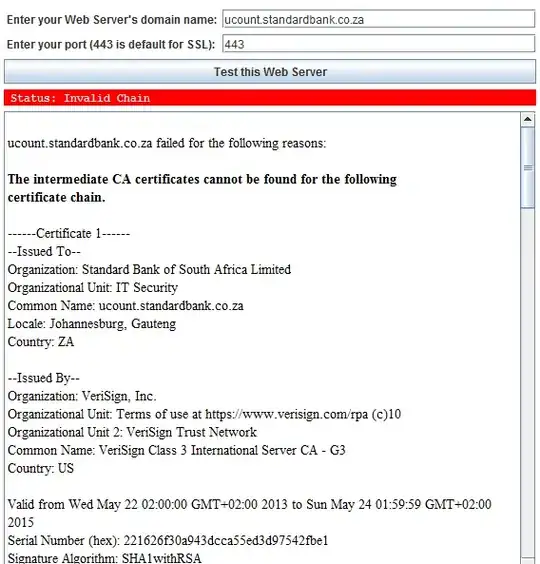
I have a very specific question.
A client verifies a server by taking the certificate and checking specific values and that the digital signature of the intermediate CA is correct (according to the public key stored on the clients computer).
- Option A: Does the client not make sure that the intermediate CA signature (signed by the root CA) is valid, and that the root digital signature (self signed by the root CA) correlates with the public key stored on the computer?
OR
- Option B: Does the client see that the digital signature of the server is correct and therefore uses the information stored in the certificate store to make up the rest of the chain (i.e. if Certificate B was used to sign the server certificate then my certificate store says that certificate A was used to sign certificate B and therefore I will show that as the rest of the chain)
I understand that the entire chain is installed on the server, but does the client use all certificates?
This was sparked by my general interest and I experienced a case where the intermediate certificate was not installed properly and Google Chrome and Internet Explorer accepted it but Firefox 4.0 did not.
I hope I made my question as clear as possible.
I have taken out some of the other steps used in SSL validation on purpose as not to confuse the question.
Note: There was an invisible image associated with this question which I discovered when editing: