In the "Dump" section at the bottom of x64dbg / x32dbg, you can right click and select "Find Pattern". In there you can search for ASCII, Unicode (UTF-16), or UTF-8 encoded strings in memory.
Cheat Engine is another very useful tool for memory scanning, and may be more appropriate if you're trying to find a specific bit of memory with contents that change periodically.
If the executable is simply checking that the string you entered matches a hard-coded one, you don't need to do anything - just enter that text and you win.
If the executable is doing a more complex check you might want to just patch it to always pass regardless of whether the correct key is entered. This is usually done by finding the conditional jump that checks whether the key was valid (e.g. jz, jnz, jbe, etc.) and patching it to an unconditional jump (jmp) or removing the jump entirely (replace it with nop).
For example, this code checks whether rax is zero, and if so it jumps to a failure case:
48 85 C0 test rax, rax
75 1F jnz fail
Since you never want it to fail, you'd replace the jnz fail with a pair of nop instructions:
48 85 C0 test rax, rax
90 nop
90 nop
Sometimes you'll run into the opposite case. This code tests if rax is equal to 4, and jumps to a success case if it is:
48 83 F8 04 cmp rax, 4
74 2A jz success
Since you always want it to succeed, you can swap the jz out for a jmp:
48 83 F8 04 cmp rax, 4
eb 10 jmp success
What the exact instructions are doing, which conditional jump you want to patch, and which type of patch you want to do is down to the specific situation. That's the challenge. You'll have to figure that part out on your own :)
Press spacebar while highlighting an instruction in x32dbg or x64dbg to edit that instruction. You can then type in a replacement instruction. If you tick the "Keep Size" option, it will prevent you from accidentally overwriting the next instruction by entering a replacement instruction that is too large. If you check the "Fill With NOPs" box, it will pad the leftover space with bytes if you enter an instruction that encodes to something smaller than the instruction you're overwriting.
Once you've made your changes you can save the patched copy of the file. Go to File -> Patch File (Ctrl+P) to see a list of the changes you've made. If you don't want to include certain changes, you can untick them.
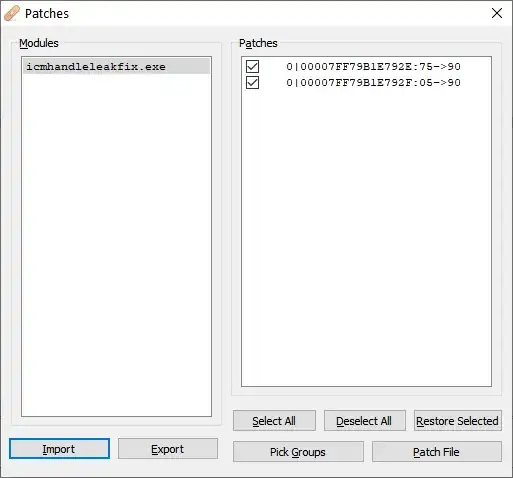
When you've picked which changes you want to apply, click Patch File in the bottom right to patch the file on disk.
