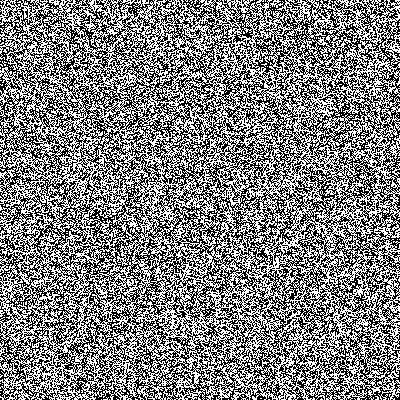
I know that PHP used the system implementation for its rand() function, which is usually a weak LCG or LFSR implementation. Did this change?
In case it still does, I am using Fedora 32.
PHP states in its documentation that rand() does not create cryptographically secure values.
I've written a small script, that creates a 400x400px PNG by randomly coloring pixels black or white:
<?php
$resolution = 400;
header("Content-type: image/png");
$im = imagecreatetruecolor($resolution, $resolution)
or die("Cannot Initialize new GD image stream");
$white = imagecolorallocate($im, 255,255,255);
for ($y = 0; $y < $resolution; $y++) {
for ($x = 0; $x < $resolution; $x++) {
if (rand(0, 1)) {
imagesetpixel($im, $x, $y, $white);
}
}
}
imagepng($im);
imagedestroy($im);
?>
I cannot see patterns anymore when using the function in PHP7.3 though. May there be patterns at a level I cannot display in my experiment?
rand():
for use where unbiased results are critical
according to PHP's docs