There is something which is bothering me when i think about the CA cert and Local cert.
Below are my queries which pertains to juniper but may be generic as well.
1) "request security pki ca-certificate enroll ca-profile ROOT2" The above is used to get the CA certificate from the CA server if I am not wrong. And the same(certificate) is used to confirm that its indeed a trusted CA server. But what does the cert actually contain? How does the device know that its the intended CA server?
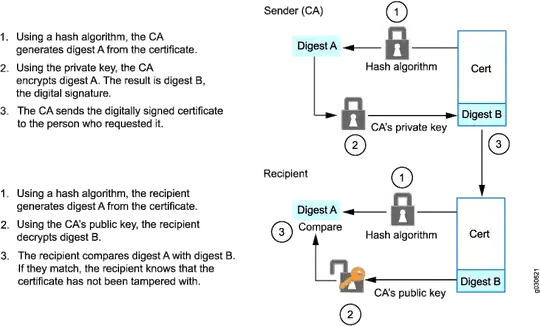
The above diagram shows how the Recipient receives the Cert and decrypts it using the CA's public key. But how does the Recipient know about the public key and the Hash algorithm?
->Is that negotiated separately before all this happens?
-> And does that happen in clear-text?
->And also, is it a one time thing, as in is the CA cert loaded onto the router and is used only once to just authenticate the CA server or is it used again during any time of the traffic flow between the IPSec peers?
2) "request security pki local-certificate enroll certificate-id"
In the above step, the VPN peer is requesting for a local cert.
->So, is it during this step that the CA server gets to know about the peer's public key or is it exchanged well in advance?
-> And does the above diagram hold good for the local cert as well? In this case, the cert contains the peer's public key and other info such as subject, etc and does it hash it to create a "fingerprint/digest" and again encrypts it with its private key?
-> And if the above process is correct, then do the peers again check the local cert's integrity and authenticity by decrypting using the CA's public key and then only sending it to the other peer ? If not, does it directly send the received local cert to the peer?
I couldnt get the answers for the questions asked above.
Please help me understand the same. Thanks a lot in advance.