This question is related to an earlier question I had: Encryption on Mobile Devices - Multiparty Encryption - Key Management
My situation: I have many mobile devices that want to send sensitive information to different clients by passing by the back-office which stores this information for some time. As described in the answer of my question I want to use sender keys to encrypt this sensitive information and make it accessible only for the clients. Since the communication is one-directional I have an easier key-management.
However, I am not sure if my idea of the protocol and the key updating is secure.
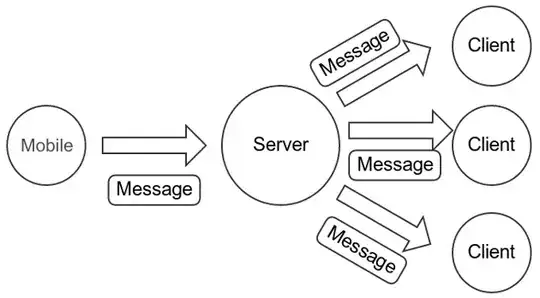
For simplicity let's only look at one mobile device A communicating with different clients C1, C2, ..., Cn.
 Source : https://signal.org/blog/private-groups/
Source : https://signal.org/blog/private-groups/
For the Setup: the back-office B passes the clients' public keys to A. Then, A generates a sender-key sk and encrypts it with each of the Ci's public keys. The Ci can decrypt and retrieve sk.
Then, when A want's to send sensitive information he encrypts it with the symmetric sk and sends it to B that stores it for some time without being able to access the information. Then B sends the encrypted information to the corresponding Ci.
To update the key sk
1st idea: A sends along with the message some update information. If a new member joins the group, we just have to send him the secret key sk encrypted with his public key.
If a member leaves the group, he will not receive the key update-information.
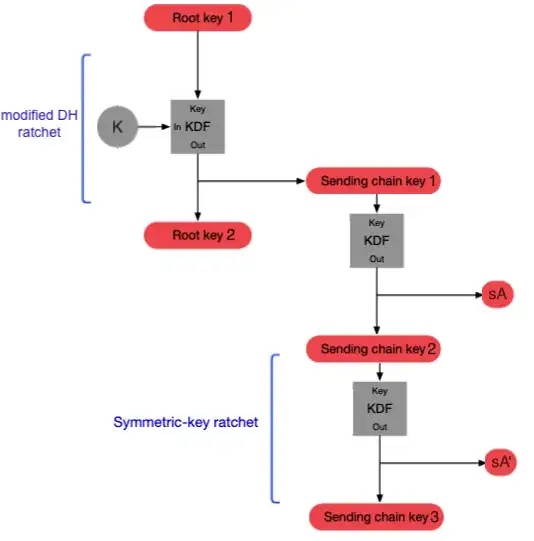
2nd idea: use a similar procedure as in the double-ratchet algorithm. A sends a secret k along with a root-key to the clients (encrypted with their public key). Then, we do a ratchet step deriving a chain-key from the secret k and the root key. Then, for each message a symmetric-key ratchet deriving a symmetric key from the chain key. This way, if a member leaves the group we send a new secret k to all the current members and derive a new chain-key. For a new member we send the current root-key to the new member and a new secret k to all group members.
Questions:
1) How expensive is the setup for many Ci?
2) Can the update information be sent unencrypted?
3) Does it suffice, if a member leaves the group, to just not send him the update information, or do I have to redo a key set-up with all the current members?
4) When we have many mobile devices A, all the clients need to store many secret keys sk. Might this be a problem? Since, if one of the Ci stores the keys insecurely they are corrupted for all the other Ci.