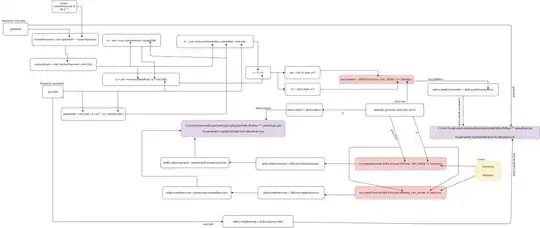
The comment by @jnylen gave a source for the algorithm.
In the data structure, item1 is the global salt, and item2 contains (in DER encoding) the entry salt and the encrypted key. This key is used to encrypt the rest of the data (per username and password).
The encryption of the master key is done with 3DES-CBC, with a key (and IV) derived from the master password, a global salt and a "per entry" salt. By default, the master password is the empty string. The password's entropy is bounded to 160 bits by sha1, which is further bounded to 112 bits by 3DES. The password is not hardened using multiple iterations of an hash.
The encryption of items (usernames and passwords) is done using 3DES-CBC, with an IV included in the metadata of each item. How IV is generated cannot be guessed from this source of the algorithm.
Unless the IVs are poorly generated, the small amount of data encrypted means that the best attack on 3DES is brute-forcing the master key or the user's password. The upper bound of 112 bits means that is this algorithm is considered weak by today standards: a big organization with huge resources might be able to brute-force the key in a few decades. Quantum computers might break them faster.
In practice, this means that a good, long passphrase must be used as the master password. This algorithm is in need a good refactoring, moving to current best practices: Argon2id with at least 128MB and 3 iterations, and an AEAD cipher (like those used in TLS 1.3).