Is it possible to have an air-gapped system which can send and receive files?
From a high level perspective, I can't seem to figure out how this can work and I am starting to think it is impossible. But before I give up, I thought I should ask the experts here if it is possible or not.
I have tried using USB drive, one way ethernet cables, public-private key pairs, web cams, ocr etc, but I can't seem to work it out.
How about using a system similar to the blockchain? The blockchain can send and receive data and remain secure, as in an off line computer can sign a transaction where the private key is safe, then the signed transaction can be broadcasted on an online computer, which means the off line private key never gets connected to an online computer.
Can this model somehow be adapted to make it possible to send and receive files in an air gapped system?
When I say "system" I mean I don't mind if I have to have multiple computers in the system to make air gap sending/receiving possible.
Here is a quick high level diagram. Any method I think of to send files between OF1 and OF2 (red dashed line) seems to compromise everything.
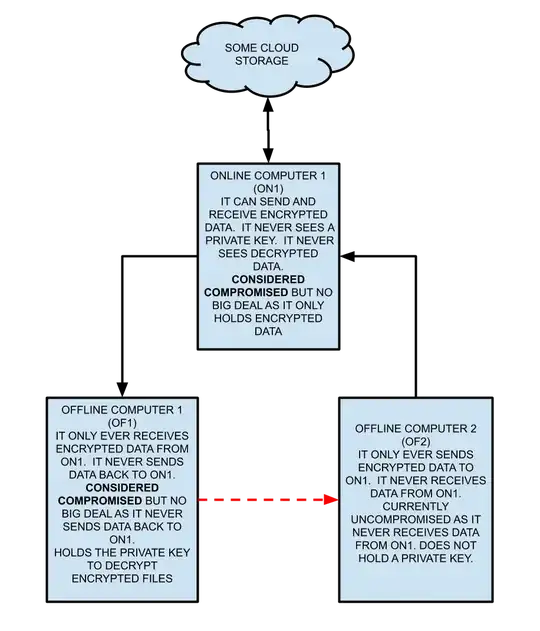 How do I send encrypted files from OF1 to OF2 without compromising everything in the system? So far, I have not be able to think of a solution.
How do I send encrypted files from OF1 to OF2 without compromising everything in the system? So far, I have not be able to think of a solution.
The difficulty for me is the red dashed line. How do I transfer a file between OF1 and OF2.
Is it even possible?